Tamera and Rupert each applied for the same credit card through the same company. Tamera has a positive credit history. Rupert has a negative credit history.
Which compares their credit limits and likely interest rates?
Answers
Answer:
it is two by five credit limit
Answer:
Your answer is A Tamera’s credit limit is most likely higher than Rupert’s, and her interest rate is most likely lower.
Explanation:
I got it right on the test and I hope this answer helps
Related Questions
If you have a really good picture of your friend, it is okay to post without asking because they allowed you to take it in the first place. O True O False
Answers
In which category would Jamal most likely find an appropriate template for his report?
Designs
Diagrams
Education
Personal
Answers
Answer:
Education
Explanation:
What is 4÷15-18×27.6
Answers
HELP !!!
Which of the following statements best represents the difference in printing text and images in the era of moveable type?
Text was harder to print than images because it involved moving letters around for each line of print.
Text was created by arranging letter blocks, while images were created through an engraving process.
Text was created by engraving letter blocks on metal, while images were created by burning imprints onto wood.
Text was easier to print than images because it involved the same 26 letters used over and over.
Answers
Answer:
I think the answer is: Text was created by arranging letter blocks, while images were created through an engraving process.
Explanation:
in the article it explains these were the ways text and images were printed
Answer:
e
Explanation:
How do technologies such as virtual machines and containers help improve
operational efficient?
Answers
Answer:
Through the distribution of energy usage across various sites, virtual machines and containers help to improve operational efficiency. A single server can accommodate numerous applications, negating the need for additional servers and the resulting increase in hardware and energy consumption.
Hope this helps! :)
WHICH OF THE FOLLOWING TASKS ARE PART OF THE SOFTWARE EVALUATION PROCESS?
TESTERS...
Answers
With regard to software evaulation, note that the correct options are -
Testers check that the code is implemented according to the specification document.A specification document is created.Any issues with the software are logged as bugs.Bugs are resolved by developers.How is this so?The tasks that are part of the software evaluation process include -
Testers check that the code is implemented according to the specification document.A specification document is created.Any issues with the software are logged as bugs.Bugs are resolved by developers.Tasks not directly related to the software evaluation process are -
Software developers writing code line by line.Creating a design for the software program.Learn more about software evaluation at:
https://brainly.com/question/28271917
#SPJ1
Full Question:
Although part of your question is missing, you might be referring to this full question:
Choose all that apply: Which of the following tasks are part of the software evaluation process?
testers check that the code is implemented according to the specification document
an specification document is created
software developers write code line by line
any issues with the software are logged as bugs
bugs are resolved by developers
a design for the software program is created
Discuss at least 1 Miscrosoft Windows security features that could protect data.
Answers
Answer:
Virus & threat protection.
Explanation:
Monitor threats to your device, run scans, and get updates to help detect the latest threats.
Answer:
User account control.
Explanation:
prevents malware damage. Helps organizations deploy a better-managed desktop.
Among the following, which is the best protection against ransomware?
Windows File History
Carbonite
Keylogger software
Authy by Twilio
Answers
Answer:
A
Explanation:
windows file history
In Java only please:
4.15 LAB: Mad Lib - loops
Mad Libs are activities that have a person provide various words, which are then used to complete a short story in unexpected (and hopefully funny) ways.
Write a program that takes a string and an integer as input, and outputs a sentence using the input values as shown in the example below. The program repeats until the input string is quit and disregards the integer input that follows.
Ex: If the input is:
apples 5
shoes 2
quit 0
the output is:
Eating 5 apples a day keeps you happy and healthy.
Eating 2 shoes a day keeps you happy and healthy
Answers
Answer:
Explanation:
import java.util.Scanner;
public class MadLibs {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
String word;
int number;
do {
System.out.print("Enter a word: ");
word = input.next();
if (word.equals("quit")) {
break;
}
System.out.print("Enter a number: ");
number = input.nextInt();
System.out.println("Eating " + number + " " + word + " a day keeps you happy and healthy.");
} while (true);
System.out.println("Goodbye!");
}
}
In this program, we use a do-while loop to repeatedly ask the user for a word and a number. The loop continues until the user enters the word "quit". Inside the loop, we read the input values using Scanner and then output the sentence using the input values.
Make sure to save the program with the filename "MadLibs.java" and compile and run it using a Java compiler or IDE.
What is your idea for creating a new and fresh Gaming experience around viewing occasions for Mike's?
Answers
My idea on creating a new and fresh Gaming experience around viewing occasions is that one should incorporate emotions into games that people around around viewing occasions can feel.
What is a gaming experience?Gaming is known to be that experience or one can say the origin of identity and also the community that is made for gamers.
Note that the experience is one that goes far more than the game itself, and as such, My idea on creating a new and fresh Gaming experience around viewing occasions is that one should incorporate emotions into games that people around around viewing occasions can feel.
Learn more about Gaming experience from
https://brainly.com/question/27355039
#SPJ1
New trends and tools are continuously emerging in the field of digital media. Discuss the advantages of these trends and tools for a digital media professional.
Answers
Answer:
There are multiple ways of being recognized and known, if new trends are emerging, people will try and get the most out of it so they can be recognized. Another reason is that people can try new things, it could be a new hobby, a new liking or just something they might want to share meaning it gets more attention
Explanation:
How could you use a spreadsheet you didn't like to simplify access also the problem
Answers
Explanation:
......
Write an algorithm to find the sum of all even numbers up to given number?
Answers
Answer:
in python:
n = int ( input ( "Pick a number" ) )
total = 0
for num in range ( 0, n+1, 2 ) :
total = total + num
print ( total )
Explanation
this algorithm will calculate the sum of all even number from 0 till the number that was inputed by the user. *the reason why there is an n+1 is because in python, the number entered will not be counted. for example if there is an input of 25, this will calculate the sum of even integers from 0 to 24. so we add 1 which will get 26. so if there is an input of 25, the code will solve it from 0 to 25.
list two precautions you should take when using free utility software available on the web
Answers
Answer:
dont use any personal information. make sure its a safe website
Research and discuss the similarities and differences between cloud computing and client-server computing. Discuss the pros and cons of each.
Answers
Answer:
Cloud computing as a virtual hosting tool, is much more theoretical. Both servers, applications, and communications are hosted in the cloud, off property, rather than being available via computer machine whereas In computing client/server, a controller gets client requests mainframes and needs to share its services, programs and/or data of one sometimes more client systems on the internet, and a client would be a portable platform that specific portions with a server and make use of a finite resource.
Explanation:
Similar to cloud computing and client-server computing: -
The cloud computing and client-server networking underpinning principles are the same. That is contact between client and server. Throughout networking and client-server networking, user nodes can communicate (queries) with databases that live locally or are located in many other networks.Difference between computing and client-server computing: -
Resources: -
In computing client-server, the corporation or association controls the tools. The services are offered in cloud computing by third parties or other businesses.The purpose of cloud computing and client-server computing is different:-
Client-server computing is targeted at use. In computation, client-server clients request a product from the cloud. The operating system runs the test, then returns it. Cloud computing is a sort of system in which the IT-related services are leased to the clients as a contract.Pros and cons of Cloud Computing:-
The Pros:-
Lower costs for business:-The cloud is saving a lot of money for a medium-sized or small enterprise. Better Reliability:- A dedicated group of experts performs all programming with such a cloud computing alternative.The Cons:-
Limited Control:- When a firm stores cloud data, they have very limited control of it. There have been security issues. The cloud isn't too attuned for every company to position some information on even a cloud.Pros and cons of client-server computing:-
The Pros:-
Improved data sharing:- Data stored via the normal business method and processed on a server is available over an approved connection for the intended users. Security:- Database has stronger access control and methods to ensure data could only be accessed or abused by approved clients.The Cons:-
Overloaded Servers:- When multiple simultaneous requests from the client are made, the server is significantly overloaded, causing congestion in traffic. Impact of centralized architecture:- Because it is centralized if a vital server fails to satisfy customer requests, the client-server then lacks good network robustness.
Based on this simulator screenshot and the corresponding code block, what
is the player doing?
O A. Pressing only the "A" button
O B. Pressing both the "A" and "Menu" buttons
O C. Not pressing the "A" button
O D. Pressing both the "A" and "B" buttons

Answers
Based on this simulator screenshot and the corresponding code block, The player is Not pressing the "A" button.
What is a Simulation?A simulation is known to be the start of the operation of any kind of real-world process or system in course of time.
Note that in the case above, Based on this simulator screenshot and the corresponding code block, The player is Not pressing the "A" button.
Learn more about simulator from
https://brainly.com/question/15892457
#SPJ1
Answer:
not pressing the a button
trust me i just did it
2.3.2
Explanation:
_____ is a method of drawing a scene in which an animator only creates the important key poses that point to the action and map out how the scene will unfold.
Answers
Answer:
Explanation:
Any drawing you do from real life will help you understand weight, dimension, and composition.
false
A benshi, used in Japanese animated movies, is another name for which of the following? cartoon, stop motion, narrator, fall guy.
narrator
The process of drawing each frame of a scene from the beginning, figuring out how the action will unfold along the way is known as which of the following?
main purpose drawing
The magic lantern is the name of a magician's trick. T/F
false - name of camera
which of the following are used to draw action?
arcs
Appeal encompasses elements of good design, good drawing, and good storytelling.
true
What was an early 20th century variety show that used animation?
carnival
Magic lanterns used a light reflecting off a mirror and through a lens to project a painted image.
T
What are the key points in the actions called?
key frames.
Which of the following was a glass disc that had images painted around the outside edge
zoopraxiscope.
Flip books are very complicated to make.
T
What device used a series of images on celluloid, viewed through an eyepiece by one person at a time?
kinetoscope
Cel animation was a labor-saving technique invented by who?
Walt Disney
A storyboard is a series of drawings with dialogue and directions to summarize a film in which of the following ways?
graphically
What is the name of the process where key points in action are mapped out as the scene is drawn?
storyboarding
Using a K-Map, simplify the sum of the minterms.

Answers
Karnaugh Map or K-Map is a pictorial method used to simplify Boolean algebra expressions and produce a minimized version of a given truth table and the simplified expression is D(B+AC)+D(AC+C) + BD.
Karnaugh Map or K-Map is a grid-like representation of truth tables that enables the user to identify patterns that correspond to logical operations of the Boolean variables.
K-Maps are useful tools for simplifying Boolean expressions.
They provide a graphical method of representing a Boolean function's truth table that simplifies the process of reducing the function using Boolean algebra.
The following steps are used to simplify the sum of the minterms using K-Map:
Construct the K-Map. In this case, since the function is a sum of minterms, we are given that the output is high whenever A=0, B=1, C=0, D=0, A=1, B=1, C=0, D=0, A=0, B=1, C=1, D=0, A=1, B=1, C=1, D=0, A=1, B=0,C=1, D=1, and A=0, B=1, C=1, D=1.
These are the cells with 1 in the map.
Group the adjacent cells containing 1s in groups of 2, 4, or 8.
Convert the groupings into Boolean expressions.
Simplify the expressions by using Boolean algebra.
The K-Map for the given sum of minterms, the two groups can be converted into Boolean expressions as follows:
Group 1: BD+ACD+ABCD
Group 2: AC+BD+BCD
Simplify the Boolean expressions by using Boolean algebra.
Group 1: BD + ACD + ABCD = D (B+AC+ABC)
= D(B+AC)
Group 2: AC + BD + BCD = D(AC+B+C) + BD = D(AC+B+C+B)
= D(AC+C)
The simplified expression is D(B+AC)+D(AC+C) + BD.
For more questions on Karnaugh Map:
https://brainly.com/question/27873494
#SPJ8
What are some ways to find out what skills you need to develop at work? Check all of the boxes that apply.
Ask a supervisor’s opinion.
Ask coworkers’ opinions.
Observe what people who have easy jobs are doing.
Attend trainings offered by the company.
Answers
Answer:
Attend traings
Explanation:
Because if you do you can learn diffent waay to do it and choose your way that you like.
ANd do not obseve poeple who has it easy
the answers are:
- ask a supervisor’s opinion
- ask coworkers’ opinions
- attend trainings offered by the company
A _____ address directs the frame to the next device along the network.
Answers
Answer:
When sending a frame to another device on a remote network, the device sending the frame will use the MAC address of the local router interface, which is the default gateway.
An unicast address directs the frame to the next device along the network.
What is network?
A computer network is a group of computers that share resources on or provided by network nodes. To communicate with one another, the computers use standard communication protocols across digital linkages. These linkages are made up of telecommunication network technologies that are based on physically wired, optical, and wireless radio-frequency means and can be configured in a number of network topologies.
The term "unicast" refers to communication in which a piece of information is transferred from one point to another. In this situation, there is only one sender and one receiver.
To learn more about network
https://brainly.com/question/28041042
#SPJ13
While setting up annetwork segment you want to check the functionality cable before putting connectors on them. You also want to meaure the termination point or damange in cable which tool used
Answers
A network is divided into several parts (subnets) using network segmentation, which creates smaller, independent networks for each segment.
What is network Segementation?Segmentation works by regulating the network's traffic flow. The term "network segmentation" should not be confused with "microsegmentation," which limits east-west communication at the workload level in order to lower an organization's network attack surface.
Despite having some uses, microsegmentation should not be confused with standard network segmentation.
A network is divided into several zones via network segmentation, and each zone or segment is independently managed. To regulate what traffic is allowed to pass through the segment and what is not, traffic protocols must be used.
Dedicated hardware is used to create network segments that are walled off from one another and only permit users with the proper credentials to access the system.
Therefore, A network is divided into several parts (subnets) using network segmentation, which creates smaller, independent networks for each segment.
To learn more about network, refer to the link:
https://brainly.com/question/15088389
#SPJ1
What method is used in the following line of code to associate clicking the left button with the event handler "clickSingle"?
widget._____(' ', clickSingle)
eventHandler
eventHandler
attach
attach
connect
connect
bind
Answers
Answer:
Bind
Explanation:
widget.bind('<Button-1>', clickSingle)
Please don't answer if you don't know Type the correct answer in the box
. Spell all words correctly. How does SQA differ from SQC? SQA involves activities to evaluate software processes, and SQC involves activities that ensure quality software.
Answers
Software Quality Assurance (SQA) and Software Quality Control (SQC) are two distinct aspects of quality management in software development, each with its own focus and activities.
How different are they?SQA encompasses efforts directed toward assessing and enhancing the procedures of software development at every stage. The main emphasis is on guaranteeing that appropriate techniques, norms, and protocols are adhered to in order to create software of superior quality. SQA encompasses various tasks, including scrutinizing requirements, conducting process audits, and administering quality control procedures.
Conversely, SQC pertains to actions that prioritize assuring the quality of the actual software product. This involves employing methods such as testing, inspections, and reviews in order to detect flaws and guarantee that the software satisfies the stated demands and standards. The goal of SQC is to identify and rectify any shortcomings or irregularities within the software product.
To put it succinctly, SQA focuses on assessing and enhancing the manner in which software is developed, while SQC is primarily focused on verifying the excellence of the resulting software product. SQC and SQA both play a vital role in attaining an optimum level of software quality.
Read more about software here:
https://brainly.com/question/28224061
#SPJ1
improved pet app user
Answers
By using Internet new sources of input. Determine the information that the app gets from each source of input.
One of the most critical components found currently in IT existence is the user interface. Approximately 90 % of people are mobile and electronic equipment dependent.
Thus, software production was the idea that's happening. Thus, a better customer interface is required to boost output in application development. They have to think of it and create an app with consumers or the performance.
Learn more about internet on:
https://brainly.com/question/13308791
#SPJ1
The complete question will be
Help meeeee - Improved Pet App
Try out the improved version of the pet app that gives the user information about pet stores close by, which uses new sources of input. Determine the information that the app gets from each source of input.
User
Phone Sensors
Internet
the study of sound and sound wave is called
Answers
Answer: Acoustics
Explanation:
Acoustics is simply refered to as a branch in physics that studies sound and its wave.
Acoustics studies mechanical waves in liquid, solid state or gaseous state. Topics such as infrasound, vibration and ultrasound are studied. Someone who works in the acoustics field is referred to as an acoustician.
Which algorithm steps correctly solve the problem: How many occurrences of 2 exist in the array?
(1) increment counter if 2 is found (2) loop through array (3) inspect each array element
(1) inspect each array element (2) loop through array (3) increment counter if 2 is found
(1) loop through array (2) increment counter if 2 is found (3) inspect each array element
(1) loop through array (2) inspect each array element (3) increment counter if 2 is found
Answers
The correct algorithm steps to solve the problem "How many occurrences of 2 exist in the array?" is:
(1) loop through array(2) inspect each array element(3) increment counter if 2 is foundTherefore, option (4) is the correct sequence of steps:
Why is this correct?This is because you need to traverse the entire array and inspect each element to check if it is equal to 2. If an element is equal to 2, then you increment the counter.
1) loop through array
(2) inspect each array element
(3) increment counter if 2 is found
Read more about algorithm here:
https://brainly.com/question/24953880
#SPJ1
C++ PLEASE HELP... I ALREADY HAVE CODE WRITTEN BUT IM NOT GETTING THE CORRECT OUPUT!!!
Write code to read a list of song durations and song names from input. For each line of input, set the duration and name of newSong. Then add newSong to playlist. Input first receives a song duration, then the name of that song (which you can assume is only one word long). Input example: 424 Time
383 Money
-1
"The issue is I keep getting two spaces after '_' instead of just one."
HINTS:
"songDuration is assigned with the first song's duration before the while loop. The while loop checks if songDuration is greater than or equal to zero. If so, the while loop is entered.
The following operations are repeated in the while loop:
songName is assigned with the song's name.
Then, newSong.SetDurationAndName() sets newSong's duration and name data members.
push_back() appends newSong to playlist.
songDuration is assigned with the next song's duration.
The while loop continues to add songs to playlist until songDuration is assigned with a value less than zero."
#include
#include
#include
using namespace std;
class Song {
public:
void SetDurationAndName(int songDuration, string songName) {
duration = songDuration;
name = songName;
}
void PrintSong() const {
cout << duration << " - " << name << endl;
}
int GetDuration() const { return duration; }
string GetName() const { return name; }
private:
int duration;
string name;
};
int main() {
vector playlist;
Song newSong;
int songDuration;
string songName;
unsigned int i;
cin >> songDuration;
while (songDuration >= 0) {
//code goes here
getline(cin, songName);
newSong.SetDurationAndName(songDuration, songName);
playlist.push_back(newSong);
//code ends
cin >> songDuration;
}
for (i = 0; i < playlist.size(); ++i) {
newSong = playlist.at(i);
newSong.PrintSong();
}
return 0;
}
MY OUTPUT:
163 - Breathe
413 - Time
383 - Money
123 - Eclipse
OUTPUT:
163 - Breathe
413 - Time
383 - Money
123 - Eclipse
PLEASE HELP- thank you
Answers
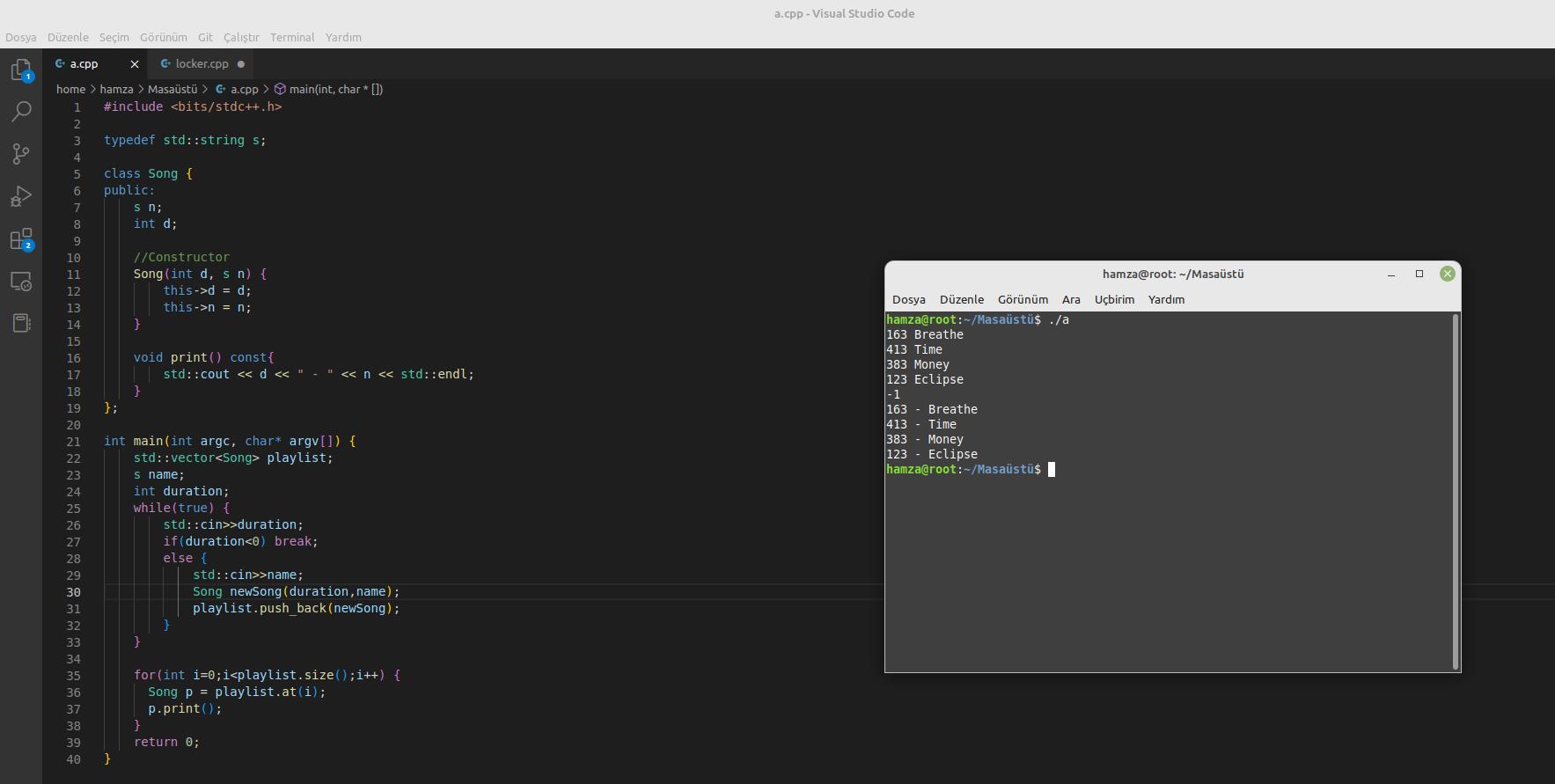
By writing the getter() and setter() methods without using them, you extend the runtime of the program. Also, the -Wunused-variable marker is automatically used by your compiler. I edited your code for you, there is no problem.
#include <bits/stdc++.h>
typedef std::string s;
class Song {
public:
s n;
int d;
//Constructor
Song(int d, s n) {
this->d = d;
this->n = n;
}
void print() const{
std::cout << d << " - " << n << std::endl;
}
};
int main(int argc, char* argv[]) {
std::vector<Song> playlist;
s name;
int duration;
while(true) {
std::cin>>duration;
if(duration<0) break;
else {
std::cin>>name;
Song newSong(duration,name);
playlist.push_back(newSong);
}
}
for(int i=0;i<playlist.size();i++) {
Song p = playlist.at(i);
p.print();
}
return 0;
}
4. What information is in the payload section of the TCP segments?
Answers
The actual data being transferred, such as the content of a web page, an email message, or a file transfer, is contained in the payload part of the TCP segments.
The content of a TCP segment is what?A segment header and a data chunk make up a TCP segment. There are ten required fields and one optional extension field in the segment header (Options, pink background in table). The payload data for the application is carried in the data section, which comes after the header.
What is the TCP Wireshark payload size?In established mode, a packet's maximum payload size is 1448 bytes (1500 - 20 IP header - 32 TCP header).
To know more about data visit:-
https://brainly.com/question/29851366
#SPJ1
What is the impact of social media on mainstream media?
Answers
Answer:
Allows you to interact and engage with other people who are interested in the same topic.
Explanation:
This is so because it is not one sided.
what is the full form of Cobol
Answers
COBOL (Common Business-Oriented Language) is a high-level programming language for business applications. It was the first popular language designed to be operating system-agnostic and is still in use in many financial and business applications today.