although our capacity for storing information is large, we are still limited in the number of permanent memories we can form. true or false
Answers
The statement is true. Although the human brain has an enormous capacity to store information, there is a limit to the number of permanent memories that we can form.
This limit varies from person to person and is influenced by factors such as age, genetics, and lifestyle. The brain stores information in two types of memory: short-term and long-term memory. Short-term memory can hold a limited amount of information for a short period of time, usually less than 30 seconds. Long-term memory, on the other hand, has a virtually unlimited capacity but requires repetition and consolidation to become a permanent memory. While our brain can store an immense amount of information, it is important to remember that the ability to form and retain long-term memories is not infinite, and we may experience difficulties with memory as we age or due to certain medical conditions.
Learn more about information here:
https://brainly.com/question/31102538
#SPJ11
Related Questions
The real power of data validation becomes apparent when you use data validation formulas. The formula that you specify must be a logical formula that returns either true or false. If the formula evaluates to true, what does it mean?.
Answers
What a user can enter into a cell can be regulated with the use of data validation. Examples of common scenarios that you might encounter are covered in these formulas.
What is a formula for data validation?Validating data to prevent duplication and only permit unique entries. The formula returns TRUE and the validation is successful when a singular value is entered. When the input cannot be validated because the same value already exists in the range supplied (count larger than 1), COUNTIF returns FALSE.
How may data validation be used in an equation?To a cell or range, add data validationTo validate, pick one or more cells.Click Data Validation under the Data Tools section of the Data tab.Select List in the Allow box on the Settings tab.Type your list values in the Source box, separating them with commas.The In-cell dropdown check box must be selected.To learn more about 'Data validation' refer to
https://brainly.com/question/20411239
#SPJ4
a bushing is a component that rotates within a sheave. true false
Answers
The given statement "a bushing is a component that rotates within a sheave" is false. A bushing is a component that rotates within a hole or bore. to the given question is: False: A bushing is a cylindrical lining made of metal, rubber, or nylon that is used to reduce friction and wear within a hole or bore.
A bushing is a type of bearing that is frequently used to support a rotating shaft. The bushing is commonly used in machines to reduce friction between two surfaces that would otherwise cause wear and tear. In a sheave, the rotating part is the shaft and the static part is the sheave. Hence, the given statement "a bushing is a component that rotates within a sheave" is false.
To know more about reduce visit:
https://brainly.com/question/32701670
#SPJ11
Analyze the following code.
import java.util.*;
public class Test {
public static void main(String[] args) throws Exception {
TreeSet set = new TreeSet<>();
set.add("Red");
set.add("Yellow");
set.add("Green");
set.add("Blue");
SortedSet temp = set.tailSet("Purple");
System.out.println(temp.first());
}
}
A. The program displays Red
B. The program displays Blue
C. The program displays Green
D. The program displays Yellow
E. The program displays Purple
Answers
According to the question, the following code is the program displays blue.
What is code?Code is a set of instructions or commands used to create a program, application, or website. It is the language used to communicate between computer hardware and software. Code is written by a programmer or developer who understands the language, logic, and syntax of the code. Code is written in various languages such as HTML, CSS, JavaScript, and more.
This code creates a TreeSet called "set" and adds four strings to it. It then creates a SortedSet called "temp" and sets it to the tailSet of "set" beginning at "Purple". The first() method is called on the "temp" set and the program prints the result. Since "Purple" is not in the set, this sets the start of the tailSet to "Blue" and the program prints "Blue".
Therefore, B is correct.
To learn more about code
https://brainly.com/question/30317504
#SPJ1
write a select statement that uses the view that you created in exercise 5 to get the sum of the order total for the five best selling products.
Answers
SELECT SUM(OrderTotal) FROM program vw_Top5Products ORDER BY Quantity DESC LIMIT 5;
This SELECT statement uses the view created in Exercise 5, vw_Top5Products, to get the sum of the OrderTotal for the five best selling products. It first orders the products by Quantity in descending order, and then limits the results to the top five. This will give the total OrderTotal for the five best selling products. This statement can be useful for getting a total amount of sales for the top selling products in a particular store or region. This information can then be used for comparison or for reporting purposes. Additionally, this SELECT statement can be modified to include other criteria to get more specific information regarding the top five selling products. For example, the WHERE clause can be used to filter the results to a specific store or region, or the ORDER BY clause can be changed to sort by other criteria.
Learn more about program here-
brainly.com/question/11023419
#SPJ4
Choose the correct answer
1. Which of the variable names given below, is invalid?
O Goodluck
O
d2420
O input
O Abcd
Answers
not valid bro so u check again
Match the following begging programming terms to the correct definition
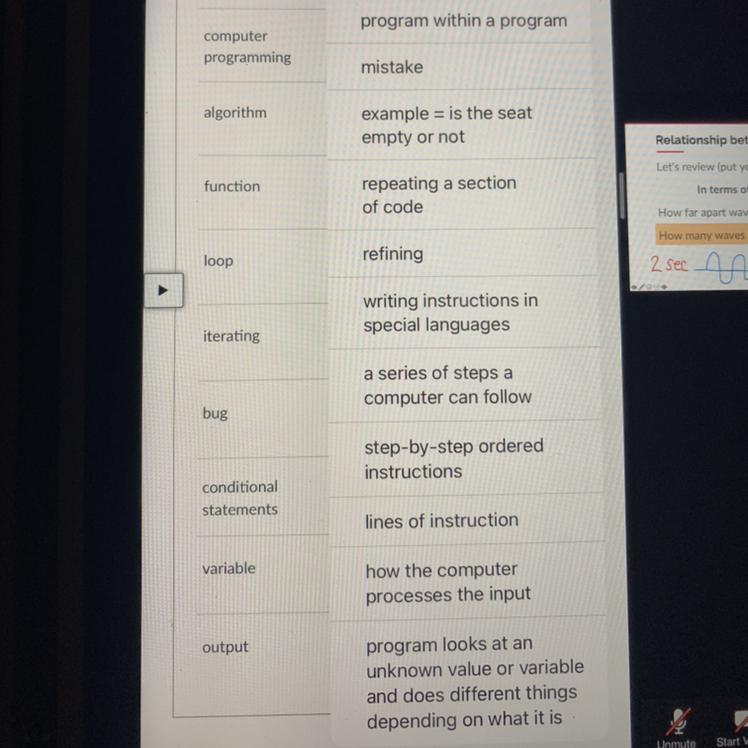
Answers
Answer:
• function - program within a program
• bug - mistake
• loop - repeating a secton of code
• iterating - refining
• conditional statements - writing instructions in special languages
• computer programming - a series of steps a computer can follow
• algorithm - step-by-step ordered instructions
• output - how the computer processes the input
• variable - program looks at an unkown value or variable and does different things depending on what it is.
Explanation:
HOPE THIS HELPS :)
PlEASE HELP!
Identify in the space below three rules you feel are most important for deciding what personal information is
appropriate to post online.
Answers
Answer:
.
Names. Be careful how you use your name. Avoid using your full name. Even a nickname could spell trouble -- for instance, if it says something suggestive about your character, if it's a name you already use with others who know your real identity, or if it's made up from your real name (say, from your initials). First names are best, unless yours is extremely unusual. These days, many people do use their full names for online posting -- on social media sites and blogs for example. Just know that in doing so you're raising the risk of becoming an identity theft victim.
Photos. Bearing in mind Golden Rule #1, don't post photos you wouldn't want everyone to see. Full face, high resolution photos may be "snagged" (copied) and used for identity theft. Some people don't know how easy this is to do with any photo, with just a couple of clicks. Also, as a matter of etiquette, don't post photos of others without their permission, unless you're prepared for the consequences if the other person doesn't think it's funny. For preference, use photos in which identities are obscured. And, as a general rule, don't post photos of children online (especially not other people's children without permission). If you want to share photos of your kids, put them in a private online album, accessible by invitation or password. Or email them directly to your friends.
Explanation:
When the computer translates digital information to information humans can use, it is called.
Answers
Or you may be looking for the term User Interface or (UI)
The score of students in a subject is inserted in B2 cell and the passing score for the subject is 60. Which of these functions will you insert in C2 cell to check if the student has passed or failed?
a.
=IF(B2>=60, "Pass", "Fail")
b.
=OR(B2>=60, "Pass", "Fail"
c.
=AND(B2>=60, "Pass", "Fail")
d.
=NOT(OR((B2>=60, "Pass", "Fail"))
Answers
The function that you will insert in C2 cell to check if the student has passed or failed is A. =IF(B2>=60, "Pass", "Fail").
What is a function?A function is simply a "chunk" of code that you can reuse instead of writing it out multiple times. Programmers can use functions to break down or decompose a problem into smaller chunks, each of which performs a specific task.
Every programming language allows you to write code blocks that, when called, perform tasks.
We have a passing mark is 60 which means marks 60 or above means to pass and less means fail.
So, We need condition using which can be done using IF statement which has syntax as below
=IF (logical_test, [value_if_true], [value_if_false])
Here, logical_test = B2>=60 (marks in B2 should be greater than or equal to 60)
[value_if_true] = "Pass"
[value_if_false] = "False"
This is illustrated as =IF(B2>=60,"Pass","False").
In conclusion, the correct option is A.
Learn more about computer on:
https://brainly.com/question/24540334
#SPJ1
pa 11-3 (static) kooyman hardware sells a ladder. they had... kooyman hardware sells a ladder. they had 5 ladders at the start of the week but demand was for 6 ladders.
What was their fill rate for this ladder?
Answers
The fill rate for a product is the percentage of demand that is met with available inventory.
In this case, Kooyman Hardware had 5 ladders at the start of the week and demand was for 6 ladders. Since they did not have enough inventory to meet the entire demand, the fill rate would be:
(fill rate) = (quantity filled) / (demand) * 100%
(quantity filled) = 5 ladders (since that is all they had)
(demand) = 6 ladders
(fill rate) = 5/6 * 100% = 83.33%
Therefore, Kooyman Hardware's fill rate for this ladder was 83.33%.
For more questions like hardware visit the link below:
https://brainly.com/question/29857377
#SPJ11
an administrator has established a secure shell (ssh) tunnel and is connecting to the remote desktop protocol (rdp) service on desktop 2. which output will display after running the netstat -a command on the secure shell (ssh) server? (eo: 8.2)
Answers
After an administrator has established a secure shell (SSH) tunnel and is connecting to the remote desktop protocol (RDP) service on desktop 2, running the netstat -a command on the SSH server will display an output that includes an active SSH connection between the administrator's computer and the SSH server, as well as a connection to the RDP service on desktop 2. The output will show the IP addresses and port numbers of the connected devices.
When accessing a computer over a network, system administrators need a secure connection to hide from malicious cyber-attacks, such as password-sniffing. As large networks have security flaws, encryption protocols such as TLS/SSL, IPsec, S/MIME, PGP, and SSH are necessary to ensure necessary protection.The acronym SSH stands for "Secure Shell." The SSH protocol was designed as a secure alternative to unsecured remote shell protocols. It utilizes a client-server paradigm, in which clients and servers communicate via a secure channel.
The SSH protocol has three layers:
The transport layer. Ensures secure communication between the server and the client, monitors data encryption/decryption, and protects the integrity of the connection. It also performs data caching and compression.
The authentication layer. Conducts the client authentication procedure.
The connection layer. Manages communication channels after the authentication.
learn more about SSH server here:
https://brainly.com/question/16182741
#SPJ11
What are the inputs that the model uses to make decisions?
Answers
Answer:
It makes the decision better and adds ownership in the implementation
Explanation:
Hope this helps C:
~Chiena
blocking everything and allowing only what is needed is known as:
Answers
Blocking everything and allowing only what is needed is known as "whitelisting."
Whitelisting is a security practice where only pre-approved or trusted entities, applications, or processes are granted access, while all others are denied. It operates on the principle of explicitly specifying what is allowed, rather than blocking specific known threats or malicious entities. This approach helps reduce the attack surface and mitigates the risks associated with unknown or unauthorized access. Whitelisting is commonly used in network security, software applications, and system administration to enhance security and enforce strict access controls, ultimately minimizing the potential for unauthorized or malicious activity.
Learn more about Whitelisting here:
https://brainly.com/question/30360318
#SPJ11
What is the final value of x (after this code has executed)?
int x = 0;
for (x = 0; x < 200; x++)
{
System.out.println(x);
}
Answers
Answer:
199
Explanation:
i starts at 0. One more than 0 is one. Until you get 199.
The computer is counting as seen below:
0
1
2
....
199
A device used in a star topology that keeps a table of mac addresses is called:
Answers
Answer:
Ethernet switches
Explanation:
Ethernet switches eliminate the need to broadcast communications out to all spokes on the star network. Instead, the Ethernet switch maintains a media access control (MAC) address table.
Which activity is the best example of a negative habit that may result from
heavy computer and Internet usage?
A. Playing web-based games instead using social media
B. Shopping online in order to find a gift for a friend
c. Using apps for driving directions instead of using a paper map
O D. Avoiding local friends in order to play online games
SUBMIT
Answers
Answer:
D
Explanation:
Any of these is an example, but the most drastic would be D, Avoiding local friends in order to play online games
Using a microphone to record a sound on your computer is an example of:
Answers
It is an example of an "Input device". A further explanation is provided below.
Audio input communication devices enable the user customer to transmit audio information to a technology to examine or evaluate, track record as well as execute controls.The microphones connect towards the computer's microphones connection mostly on rear of PC's. There may have been a microphones port at the very front of various PC's casings.
Learn more about input devices here:
https://brainly.com/question/11046738

leon started a project to design and create a new video game for the animation studio where he develops graphics and animations for video games and movies. which item below would be considered an overhead cost?
Answers
An overhead cost is a type of indirect cost that is not directly related to the production of goods or services.
What are leon's overhead costs?In the context of a video game project, some examples of overhead costs could include rent for the office space where the project is being developed, utilities for the office, salaries for administrative staff, and insurance for the project.
These costs are not directly related to the design and creation of the video game, but are necessary for the project to be completed.
To Know More About overhead costs, Check Out
https://brainly.com/question/20480458
#SPJ4
If you want readers to move down long web pages to find more information, you would use this type of web style:
Answers
Answer:
On a website, a navigation menu is an organized list of links to other web pages, usually internal pages. Navigation menus appear most commonly in page headers or sidebars across a website, allowing visitors to quickly access the most useful pages. Now, it would be easy to leave it there and call it a day.
Explanation:
(the triangle class) design a class named triangle that extends geometricobject. the class contains:
Answers
A class named Triangle has to be designed that extends the class GeometricObject.
The Triangle class can be designed as follows:
class Triangle extends GeometricObject {
// Variables that define the triangle's characteristics
double side1, side2, side3;
// Constructors
public Triangle(double side1, double side2, double side3) {
this.side1 = side1;
this.side2 = side2;
this.side3 = side3;
}
// Getters and Setters
public double getSide1() {
return side1;
}
public double getSide2() {
return side2;
}
public double getSide3() {
return side3;
}
public void setSide1(double side1) {
this.side1 = side1;
}
public void setSide2(double side2) {
this.side2 = side2;
}
public void setSide3(double side3) {
this.side3 = side3;
}
// Methods to calculate the perimeter and area of a triangle
public double getPerimeter() {
return side1 + side2 + side3;
}
public double getArea() {
double s = (side1 + side2 + side3) / 2;
return Math.sqrt(s * (s - side1) * (s - side2) * (s - side3));
}
}
Following attributes need to be present in the class Triangle: An instance variable named side1. Its visibility should be private. An instance variable named side2. Its visibility should be private. An instance variable named side3. Its visibility should be private. A constructor with side1, side2, and side3 as parameters. A method named get Area() that returns the area of the triangle. A method named get Perimeter() that returns the perimeter of the triangle. A method named __str__() that returns the string representation of the triangle.
Learn more about Instance variable here:
https://brainly.com/question/28265939
#SPJ11
Perform binary calculation: 110111 +101011) X 11
Answers
Answer:
10000110110
Explanation:
\(110111 +\\101011\)
______
1100010
1100010 × 2 is the same as \(1100010+\\1100010\) = 11000100
11000100 × 2 is the same as \(11000100+\\11000100\) = 110001000
110001000 × 2 is the same as \(110001000+\\110001000\\\) = 1100010000
\(1100010000\\11000100\\1100010+\\\)
_______
10000110110
In this lab, you will complete the implementation of a medical device vulnerability scoring web page. the purpose of this web page is to return a score that numerically quantifies how vulnerable a specific vulnerability is to the particular attack. the properties of the system will be selected from a group of predetermined options, where each option is a styled radio button. once options are selected for all possible properties, the web page will display the vulnerability score (and hide the warning label).
implement a function called updatescore. this function must verify that one button from each property is selected.
using javascript, add a click or change event listener to each radio button (do not add the event listener to the button label). notice that the radio buttons are hidden using css.
Answers
To complete the implementation of the medical device vulnerability scoring web page, you can follow these steps:-
1. Define the `updateScore` function in JavaScript:
```javascript
function updateScore() {
// Check that one button from each property is selected
// Calculate the vulnerability score based on the selected options
// Display the vulnerability score and hide the warning label
}
```
2. Add a click or change event listener to each radio button using JavaScript:
```javascript
// Select all radio buttons
const radioButtons = document.querySelectorAll('input[type="radio"]');
// Add event listeners to each radio button
radioButtons.forEach((button) => {
button.addEventListener('change', updateScore);
});
```
Make sure to adapt this code to your specific HTML structure and predetermined options. The `updateScore` function should be modified to handle the selected options and calculate the vulnerability score accordingly.
Learn more about web page here:
https://brainly.com/question/9060926
#SPJ11
match each option to the description of the task it accomplishes.
arrange>
shape styles>
size>
insert shapes>
wordart styles

Answers
Answer:
Follows are the solution to the given question:
Explanation:
Please find the attached file of the matching.
Arrange: In shape formatting, the "arrange" is used to provide an arrangement in the positing of the shape on the given slide.
shape styles: In shape formatting, it is used for applying a new design to the shape.
size: In shape formatting, the size is used for modifying the shape.
insert shapes: In shape formatting, the insert shape is used to add a new shape.
Wordart styles: In shape formatting, Wordart is used to provide a text design on the shape.

What is the procedure for melting point?
Answers
The procedure for melting point is as follows:
Grind the solid substance into a fine powder using a mortar and pestle.Place a small amount of the powder into a capillary tube and seal the tube with a flame.Place the sealed capillary tube into a melting point apparatus.Heat the apparatus gradually until the solid substance begins to melt.Record the temperature at which the substance begins to melt and the temperature at which the substance has completely melted.Repeat the procedure with a fresh sample of the substance to ensure accuracy.The melting point of a substance is the temperature at which it changes from a solid to a liquid state. It is an important physical property that can be used to identify and characterize substances. By following the above procedure, you can accurately determine the melting point of a substance.
Learn more about melting point:
brainly.com/question/40140
#SPJ11
thông tin giúp ích cho con người là gì
Answers
Nnbbgvjkhvnnp
Dining Philosophers problem in class uses a monitor. Implement the same solution (simulating monitors) using semaphores
monitor DiningPhilosophers
{
enum { THINKING; HUNGRY, EATING) state [5] ;
condition self [5];
void pickup (int i) {
state[i] = HUNGRY;
test(i); // Tests if chopsticks are available
if (state[i] != EATING) self[i].wait;
}
void putdown (int i) {
state[i] = THINKING;
// test left and right neighbors
test((i + 4) % 5);
test((i + 1) % 5);
}
void test (int i) {
// both chopsticks must be available
if ((state[(i + 4) % 5] != EATING) &&
(state[i] == HUNGRY) &&
(state[(i + 1) % 5] != EATING) ) {
state[i] = EATING ; // Gets chopsticks
self[i].signal () ;
}
}
initialization_code() {
for (int i = 0; i < 5; i++)
state[i] = THINKING;
}
}
Answers
Here's an implementation of the Dining Philosophers problem using semaphores instead of a monitor:
```python
from threading import Semaphore, Thread
THINKING = 0
HUNGRY = 1
EATING = 2
class DiningPhilosophers:
def __init__(self):
self.num_philosophers = 5
self.state = [THINKING] * self.num_philosophers
self.mutex = Semaphore(1)
self.s = [Semaphore(0) for _ in range(self.num_philosophers)]
def pickup(self, philosopher):
self.mutex.acquire()
self.state[philosopher] = HUNGRY
self.test(philosopher)
self.mutex.release()
self.s[philosopher].acquire()
def putdown(self, philosopher):
self.mutex.acquire()
self.state[philosopher] = THINKING
self.test((philosopher + 4) % self.num_philosophers)
self.test((philosopher + 1) % self.num_philosophers)
self.mutex.release()
def test(self, philosopher):
left_philosopher = (philosopher + 4) % self.num_philosophers
right_philosopher = (philosopher + 1) % self.num_philosophers
if (
self.state[left_philosopher] != EATING
and self.state[philosopher] == HUNGRY
and self.state[right_philosopher] != EATING
):
self.state[philosopher] = EATING
self.s[philosopher].release()
def philosopher_thread(philosopher, dining):
while True:
# Philosopher is thinking
print(f"Philosopher {philosopher} is thinking")
# Sleep for some time
dining.pickup(philosopher)
# Philosopher is eating
print(f"Philosopher {philosopher} is eating")
# Sleep for some time
dining.putdown(philosopher)
if __name__ == "__main__":
dining = DiningPhilosophers()
philosophers = []
for i in range(5):
philosopher = Thread(target=philosopher_thread, args=(i, dining))
philosopher.start()
philosophers.append(philosopher)
for philosopher in philosophers:
philosopher.join()
```
In this solution, we use semaphores to control the synchronization between the philosophers. We have two types of semaphores: `mutex` and `s`. The `mutex` semaphore is used to protect the critical sections of the code where the state of the philosophers is being modified. The `s` semaphore is an array of semaphores, one for each philosopher, which is used to signal and wait for a philosopher to pick up and put down their chopsticks.
When a philosopher wants to eat, they acquire the `mutex` semaphore to ensure exclusive access to the state array. Then, they update their own state to `HUNGRY` and call the `test` function to check if the chopsticks on their left and right are available. If so, they change their state to `EATING` and release the `s` semaphore, allowing themselves to start eating. Otherwise, they release the `mutex` semaphore and wait by calling `acquire` on their `s` semaphore.
When a philosopher finishes eating, they again acquire the `mutex` semaphore to update their state to `THINKING`. Then, they call the `test` function for their left and right neighbors to check if they can start eating. After that, they release the `mutex` semaphore.
This solution successfully addresses the dining Philosophers problem using semaphores. By using semaphores, we can control the access to the shared resources (chopsticks) and ensure that the philosophers can eat without causing deadlocks or starvation. The `test` function checks for the availability of both chopsticks before allowing a philosopher to start eating, preventing situations where neighboring philosophers might be holding only one chopstick. Overall, this implementation demonstrates a practical use of semaphores to solve synchronization problems in concurrent programming.
To know more about Semaphores, visit
https://brainly.com/question/31788766
#SPJ11
the checkpoint region (cr) is defined as: select one: a. unknown location to begin file lookups b. region used to store checkpoints c. fixed and known location on disk to begin a file lookup d. checkpoints for time hacks
Answers
The checkpoint region (cr) is defined as fixed and known location on disk to begin a file lookup.
What is the purpose of checkpoint?A significant provider of cyber security solutions to corporations and governmental organizations throughout the world is (www.checkpoint.com). With a market-leading capture rate for malware, ransomware, and other cyberattacks, its products defend consumers from 5th generation cyberattacks.The checkpoint region (CR) is a fixed and well-known position on disk where a file lookup can start. Every one of the following, with the exception of: Memory capacities had leveled off.At a checkpoint, the flow of traffic is halted to allow for inspection.A Checkpoint firewall is a device that permits interconnection of various networks in accordance with a specified security policy.To learn more about cyber security solutions refer to:
https://brainly.com/question/28004913
#SPJ4
Bluetooth is the popular name for the 802. 15 wireless networking standard, which is useful for creating small __________.
Answers
Answer:
Personal Area Networks (PANs).
With _____, human thinking and problem-solving is performed by a machine, including learning, reasoning, and self-correction. wearable technologies quantum computers artificial intelligence Moore's Law
Answers
Answer:
THE ANSWER IS B
Explanation:
what is a program answer these question
of grade-6
Answers
a series of coded software instructions to control the operation of a computer or other machine.