a user is entering a building that has an electronic locking system. the user starts an app on their phone and touches it to the lock console and then enters a pin to gain entry. which credential categories did the user use, and in what order were they used to gain entry?
Answers
The user first used their phone as a credential by starting the app and touching it to the lock console. This is an example of a credential in the "something the user has" category, as the user must physically possess the phone in order to use it as a credential.
After touching their phone to the lock console, the user then entered their PIN to gain entry to the building. This is an example of a credential in the "something the user knows" category, as the user must have knowledge of the PIN in order to use it as a credential.
Therefore, the user used the "something the user has" credential category first, followed by the "something the user knows" credential category.
Related Questions
A time-saving strategy that helps define unfamiliar words involves using
familiar words for clues.
the dictionary for clues.
online resources.
reference books.
Answers
The correct answer is A. Familiar words for clues
Explanation:
Finding unfamiliar words is common while reading, especially in texts that belong to a specific field such as medicine, technology, etc. This can be handled through multiple strategies such as using a dictionary, guessing the meaning of the word based on its parts, and using context clues.
In this context, one of the easiest and most time-saving strategy is the use of context clues that implies using the familiar words as clues to guess the meaning of an unfamiliar word. This is effective because in most cases the meaning of an unknown word can be determined using the context of the word or words around the unknown word. Also, this strategy takes little time because you only need to analyze the sentence or paragraph where the unknown word is. Thus, the time-saving strategy to define unfamiliar words involves using familiar words for clues.
Answer:
A is correcto mundo
Explanation:
What is the Multiple Source Test? (1 point) checking to make sure that information can be found in more than one place a fact checking software that tests information found on the Internet an amendment that states that all information must be in multiple locations a test that provides more than one answer possibility 2. Which of the following is a true statement? (1 point)
Answers
Answer:
there is no following options
Explanation:
Answer: The correct answer is checking to make sure that information can be found in more than one place
Explanation: Sources are defined as locations where information is stored and accessible. When researching and validating information on the Internet (or in print), it is common practice to test multiple sources to corroborate the same details (aka Multiple Source Testing).
Which of the following tripeptides carries a net positive charge at pH7.0 ? I. Gln-Val-Ser II. Ala-Thr-Asn III. Pro-lle-Leu IV. Leu-Lys-Gly V. Arg-Glu-Met
Answers
The tripeptide that carries a net positive charge at pH 7.0 is Leu-Lys-Gly (IV).
At pH 7.0, the carboxyl group of glutamic acid (Glu) in Arg-Glu-Met (V) and the carboxyl group of aspartic acid (Asp) in Ala-Thr-Asn (II) are deprotonated, resulting in a net negative charge. On the other hand, the side chain of lysine (Lys) in Leu-Lys-Gly (IV) has an amino group that can accept a proton at pH 7.0, resulting in a net positive charge. Therefore, out of the options given, Leu-Lys-Gly (IV) is the tripeptide that carries a net positive charge at pH 7.0.
Here is a summary:
- Gln-Val-Ser (I) does not contain any charged amino acids and therefore does not carry a net positive charge at pH 7.0.
- Ala-Thr-Asn (II) contains aspartic acid (Asp), which has a deprotonated carboxyl group and carries a net negative charge at pH 7.0.
- Pro-Ile-Leu (III) does not contain any charged amino acids and therefore does not carry a net positive charge at pH 7.0.
- Leu-Lys-Gly (IV) contains lysine (Lys), which has an amino group that can accept a proton at pH 7.0, resulting in a net positive charge.
- Arg-Glu-Met (V) contains glutamic acid (Glu), which has a deprotonated carboxyl group and carries a net negative charge at pH 7.0
So, the answer is option IV
Learn more about tripeptide at:
https://brainly.com/question/31827580
#SPJ11
A business might want to use virtual machine to
allow outside customers access to files
completely eliminate physical servers
easily secure the company intranet
remotely maintain servers
Answers
Answer:
Allow outside customers to access files
Explanation:
A VM doesn't eliminate the need for additional load balancing hardware, an intranet is maintained with multiple computers typically, and remotely maintaining servers can be accomplished with SSH.
The reason you would want a VM for outside customer access is so that they can't interfere with anything outside of the sandboxed environment, this helps to mitigate hacking and easily isolate specific customer information.
A business might want to use virtual machine to allow outside customers access to files, completely eliminate physical servers, easily secure the company intranet, and remotely maintain servers.
What is virtual machine?A virtual machine (VM) is a software-based emulation of a computer system, allowing a physical computer to run multiple operating systems and applications simultaneously.
A business might want to use virtual machines to:
Allow outside customers access to files: A virtual machine can be set up to provide external customers access to specific files or applications without compromising the security of the company's internal network.
Completely eliminate physical servers: Virtual machines allow multiple operating systems to run on a single physical server, reducing the need for physical hardware and saving costs on maintenance and power consumption.
Easily secure the company intranet: Virtual machines can be used to create a secure network environment that can be easily managed and isolated from the rest of the network.
Remotely maintain servers: Virtual machines can be managed and maintained remotely, which allows IT staff to perform tasks without having to be physically present at the server location. This can save time and reduce costs associated with travel and on-site maintenance.
Thus, all options are correct.
For more details regarding business, visit:
https://brainly.com/question/15826604
#SPJ2
who is the father of computer
Answers
Answer:
Charles Babbage
Explanation:
An exceptionally gifted scientist, mathematician, economist, and engineer, Charles Babbage also invented the computer. It is difficult to envision living in the twenty-first century without computers. They are all around us, simplify our lives, and are found everywhere. Banks, government agencies, commercial businesses, and institutions engaged in space exploration all use computers.
Write the steps involving coping and pasting a file in a folder
Answers
Answer:
You single click on a file to get the file "selected". Then you hit the command sequence "Ctrl + C" on Windows OS or "Command + C" on MacOS.
You can alternatively right click on a file to open up some options which includes Copy.
You then enter the chosen folder and click on the white space.
You can then do "Ctrl + V" on Windows or "Command + V" on MacOS.
Alternatively, you can right click and locate the paste option.
Explanation:
pls, help it's urgent... 44 points plsssssssssssssssss
Write an algorithm and Flowchart for reversing a Number eg. N=9486.
Answers
The steps to reverse a number is given below:
The AlgorithmStep 1 Start
step 2 Read a number n
Step 3 a=n/1000
step 4 calculate b=(n%1000)/100
step 5 calculate c= (n%100)/10
step 6 calculate d = n%10
step 7 calculate reverse = a+(b*10)+(c*100)+(d*1000)
step 8 display reverse
step 9 stop
Read more about algorithms here:
https://brainly.com/question/24953880
#SPJ1
what is the full form of CCTV
Answers
Answer:
CCTV stands for closed-circuit television
A Linux administrator is testing a new web application on a local laptop and consistently shows the following 403 errors in the laptop's logs: The web server starts properly, but an error is generated in the audit log. Which of the following settings should be enabled to prevent this audit message?
Answers
New web application on a local laptop and consistently gets the 403 errors in the laptop's logs, they should enable the 'setenforce 0' command to prevent this audit message.
Read below to get a detailed answer on the topic:Linux, being an open-source operating system that is widely used, contains many web servers that have become popular in recent times. To test web applications, Linux administrators often employ local laptops. If the administrator receives a 403 Forbidden error, this indicates that the server understands the request but refuses to authorize access due to insufficient permissions.The audit log will be updated with an error message if the administrator cannot access the application. The SELinux configuration can be used to troubleshoot the issue. The Linux administrator can utilize the 'setenforce 0' command to avoid the audit message. The command will put SELinux into permissive mode, which will allow the application to continue to run, but it will not be given any permissions.
The setenforce 1 command is used to turn on SELinux, while the setenforce 0 command is used to turn it off. By default, SELinux is set to enforcing mode in Linux. When SELinux is in enforcing mode, all security policies are enforced, and any policy violations will result in an error message.
Therefore, enabling the 'setenforce 0' command is necessary to avoid audit messages when troubleshooting the issue of the 403 Forbidden error while testing a web application on a local laptop in Linux.
Learn more about operating system :
https://brainly.com/question/31551584
#SPJ11
A cycle merchant allows 15% discount on the marked price of a bicycle and still he makes a profit
of 20%. Write a program to calculate Marked price and Cost price of cycle if the he offers Rs. 600 as
discount to the customer.
in java program
please do it
Answers
Answer:
The program in Java is as follows:
public class Main{
public static void main(String[] args) {
double discount_percent = 0.15;
double discount_amount = 600;
double profit = 0.20;
double marked_price = discount_amount/discount_percent;
double cost_price = marked_price/(1 + profit);
System.out.println("Marked Price: "+marked_price);
System.out.println("Cost Price: "+cost_price);
}}
Explanation:
For explanation purpose, let
\(MP \to\) Marked Price
\(\%D \to\) Percentage discount
\(D \to\) Discounted amount
\(\%P \to\) Percentage Profit
\(C \to\) Cost Price
The marked price (i.e. selling price) is calculated discount using:
\(MP = \frac{D}{\%D}\)
The derived formula of the cost price from percentage profit and Marked Price is:
\(C = \frac{M}{1 + \%P * 100}\)
So, the explanation is as follows:
The next three lines declare and initialize the given parameters
double discount_percent = 0.15;
double discount_amount = 600;
double profit = 0.20;
Calculate marked price
double marked_price = discount_amount/discount_percent;
Calculate cost price
double cost_price = marked_price/(1 + profit);
Print marked price
System.out.println("Marked Price: "+marked_price);
Print Cost price
System.out.println("Cost Price: "+cost_price);
To view the Picture tools tab, a user must first _____.
A.select the picture
B.navigate to the View tab
C.place the cursor in the right margin
D.select the picture style
Answers
How are comments used in word?
Answers
Your browser uses a cache to keep track of the websites you visit and businesses use cookies to track your online activities. Do you think these practices invade your privacy
Answers
The use of browser caches and cookies can raise privacy concerns due to the potential tracking and information collection involved.
Do these practices compromise your privacy?In today's digital age, browsing the internet has become an integral part of our lives. However, the convenience and personalized experience offered by browsers and websites come at a cost – the potential invasion of our privacy. Browsers utilize caches to store information about the websites we visit, such as images, scripts, and even entire pages.
While this can enhance loading times and improve user experience, it also means that traces of our online activities are stored locally on our devices. Similarly, businesses employ cookies to track our behavior and gather data for various purposes, such as targeted advertising and website optimization.
Learn more about Internet
brainly.com/question/16721461
#SPJ11
why is laptop personal computer
Answers
Answer:
MARK AS BRAINLIEST! LOOK AT PICTURES!


A sensible strategy for reducing your risk for cybercrime would be to a. log onto public wifi in cafes, libraries, etc. b. throw email attachments in the trash after you have opened them and determined that they're spam. c. turn off your computer when you're not using it. d. keep the same password for all of your transactions.
Answers
A sensible strategy for reducing your risk for cybercrime would be to: c. turn off your computer when you're not using it.
Turning off your computer when you're not using it is a crucial step in reducing your risk for cybercrime. When your computer is turned off, it is disconnected from the internet and prevents any potential unauthorized access or remote attacks. This simple action can significantly minimize the chances of falling victim to cybercriminals.
Leaving your computer connected to the internet while you're not using it increases the risk of being targeted by various forms of cyberattacks. Hackers can exploit vulnerabilities in your operating system or software, launch malware attacks, or attempt to gain unauthorized access to your personal information. By turning off your computer, you create a physical barrier that effectively cuts off any potential entry points for cybercriminals.
Additionally, regularly shutting down your computer provides an opportunity for software updates and security patches to be installed. These updates often address known vulnerabilities and security flaws, making your system less susceptible to cyber threats. By keeping your computer up to date with the latest security measures, you enhance your overall protection against cybercrime.
Learn more about cybercrime
brainly.com/question/32375073
#SPJ11
Electronic medical charts make it easier for doctors to
share information on patients with other doctors.
share information on patients with the government.
communicate with patients about medical issues.
track infectious diseases through a database.
Answers
Answer:
Share information on patients with other doctors
Explanation:
Got it right on edge test
Answer:
Share information on patients with other doctors
Explanation:
A process that takes plaintext of any length and transforms it into a short code is called Group of answer choices encryption hashing symmetric encryption asymmetric encryption
Answers
Answer:
hashing
Explanation:
A hash can be used in compression which reduces the length of a plaintext sequence
3.30 LAB: Golf scores Golf scores record the number of strokes used to get the ball in the hole. The expected number of strokes varies from hole to hole and is called par (i.e. 3, 4, or 5). Each score's name is based on the actual strokes taken compared to par:
• "Eagle" number of strokes is two less than par • "Birdie": number of strokes is one less than par • 'Par": number of strokes equals par • Bogey number of strokes is one more than par Given two integers that represent par and the number of strokes used, write a program that prints the appropriate score name. Print "Error" if par is not 3,4, or 5. Ex: If the input is: 4 3 the output is: Birdie LAB ACTIVITY 3.30.1: LAB: Golf scores 0/10 LabProgram.java import java.util.Scanner; public class LabProgram { public static void main(String[] args) { Scanner scnr = new Scanner(System.in); /* Type your code here. */ } }
Answers
For this program, you need to take in two integers as input representing the par and the number of strokes used. You can use a Scanner to do this, like in the code given.
Once you have the two integers, you can use an if-else statement to compare them and print out the appropriate score name.
For example, if the par is 4 and the number of strokes is 3, you would print out "Birdie" since the number of strokes is one less than par.
Similarly, if the par is 3 and the number of strokes is 5, you would print out "Bogey" since the number of strokes is one more than par.
If the par is not 3, 4, or 5, you should print out "Error".
Here is an example of the code for this program:
import java.util.Scanner;
public class LabProgram {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
int par = scnr.nextInt();
int strokes = scnr.nextInt();
if (par == 3 && strokes == 3) {
System.out.println("Par");
} else if (par == 3 && strokes == 2) {
System.out.println("Eagle");
} else if (par == 3 && strokes == 4) {
System.out.println("Bogey");
} else if (par == 4 && strokes == 3) {
System.out.println("Birdie");
} else if (par == 4 && strokes == 4) {
System.out.println("Par");
} else if (par == 4 && strokes == 5) {
System.out.println("Bogey");
} else if (par == 5 && strokes == 4) {
System.out.println("Birdie");
} else if (par == 5 && strokes == 5) {
System.out.println("Par");
} else if (par == 5 && strokes == 6) {
System.out.println("Bogey");
} else {
System.out.println("Error");
}
}
}
Learn more about programming: https://brainly.com/question/26134656
#SPJ11
In his digital portfolio, Ben wants to locate each work he created. Where can he list details about the work in his digital portfolio?
A. résumé
B. tracking worksheet
C. reference letter
D. objective statement
Answers
Answer: it’s B
Explanation:
I just took the test and got it right. The other answer is incorrect.
By default which type of permission is assigned to users of a folder?
Answers
Answer:
Read
Explanation:
By default, Read is the permission is assigned to users of a folder?
Hope it helps!
Hi is someone in K12 online schooling?
Answers
Answer:
yes, i do online school
Explanation:
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
In the Word 2016 window, where is the Status bar located?
Answers
Answer:
The Word status bar is displayed at the bottom of your document window. Just click it. You can customize if needed, just right click on the status bar.
Explanation:
Answer:
hi
Explanation:
can someone help? is this a series circuit or a parallel circuit? and why?

Answers
Based on the information, it should be noted that the diagram is a parallel Circuit.
What is the circuit about?A series circuit is an electrical circuit where the components, such as resistors, capacitors, and inductors, are connected one after the other in a single path, so that the same current flows through each component. If one component fails or is disconnected, the entire circuit will be broken, and no current will flow
The amount of current flowing through each component in a series circuit is the same. In contrast, the components in parallel circuits are arranged in parallel with one another, which causes the circuit to divide the current flow. This is shown in the diagram.
Learn more about Circuit on;
https://brainly.com/question/24088795
#SPJ1
As part of the communication element, many websites use sophisticated computer programs called ______ which mimic human conversation using artificial intelligence.
Answers
Answer:
ai based learing i think
Explanation:
When starting up his computer, Connor notices pop-ups appearing randomly from his browser. Over time, these get worse and prevent him from using the computer. What is MOST likely the cause of this?
Answers
Answer: Sounds like he has a malware problem he should uninstall all of the potentially unwanted programs (PUPs), or run an antivirus software.
Explanation:
It's what I would do if I was in that unlikely of situations because I'm constantly aware of what I download and install. Sounds like Connor should too.
what type of software can be used to trigger automatic provisioning for a new server when existing resources are too overloaded?
Answers
There are several types of software that can be used to trigger automatic provisioning for a new server when existing resources are too overloaded like Orchestration tools, Cloud management platforms, etc.
Explain these software that are used to trigger automatic provisioning for a new server in detail?
Orchestration tools: Orchestration tools such as Ansible, Chef, and Puppet can be used to automate the deployment and configuration of new servers based on predefined scripts. These tools can monitor system performance and automatically spin up new servers when existing resources are overloaded.Cloud management platforms: Cloud management platforms such as Ama-zon Web Services (AWS), Micro-soft Azure, and Goo-gle Cloud Platform (GCP) provide features such as auto-scaling and load balancing that can be used to automatically provision new servers when existing resources are too overloaded.Container orchestration platforms: Container orchestration platforms such as Kubernetes and Docker Swarm can automatically scale up or down the number of containers running on a cluster based on demand. These platforms can also spin up new servers when needed to accommodate additional containers.Infrastructure as code (IaC) tools: IaC tools such as Terraform and CloudFormation can be used to define infrastructure resources such as servers, networks, and storage in code. These tools can automatically provision new servers when existing resources are overloaded based on predefined scaling policies.The choice of software depends on the specific requirements and infrastructure of the system being used.
To learn more about server, visit: https://brainly.com/question/30172921
#SPJ4
First Person Who Answers Fast As Possible Will Be Marked As Brainiest
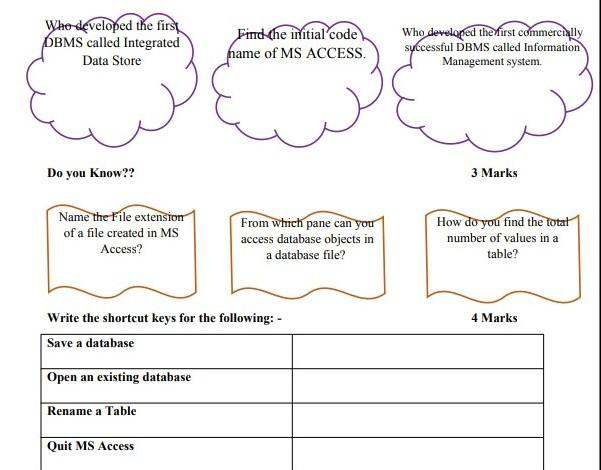
Answers
Answer:
Save a database object Ctrl+S or Shift+F12
Open an existing database Ctrl+O or Ctrl+F12
To quit MS Access ALT+F4
Explanation:
Compare the features of static and dynamic computing environments and then select the accurate statements.
a. Embedded systems are typically static, while most personal computers are dynamic.
b. A dynamic environment is easier to update than a static environment.
c. A dynamic environment gives less control to a user than a static environment.
d. Dynamic environments are easier to protect in terms of security than static environments
Answers
Compare the features of static and dynamic computing environments are options A and B:
Embedded systems are typically static, while most personal computers are dynamic.A dynamic environment is easier to update than a static environment.What is a static environment computer?A static environment is a group of circumstances, activities, and surroundings that remain constant. Once understood, a static environment doesn't provide any novel or unexpected elements. Any system that users and administrators desire to keep unmodified belongs in a static IT environment.
Note that Leading managed IT service, IT consultancy, and cyber security provider Dynamic Computing serves high-performing businesses. Our customers are small to medium-sized enterprises located locally, regionally, and nationally.
Learn more about computing environments from
https://brainly.com/question/28606168
#SPJ1
Which of the following statements best describes the
location of the Options bar?
Select one:
At the top of the workspace window, home for
essential commands, adjustments and actions
Directly beneath the Menu bar, it displays available
options for the tool selected in the Tools Panel
At the left of the workspace window, it is a column
of icons for creating and editing
At the right of the workspace, the contains the
groups of controls for working with images
Answers
The statements that best describes the location of the Options bar is
Directly beneath the Menu bar, it displays available options for the tool selected in the Tools Panel.
What is option bar?Option bar serves as a tool bar, where some functional tools can be gotten when running a program.
Therefore, option bar is located Directly beneath the Menu bar, it displays available options for the tool selected in the Tools Panel
Learn more about options bar at;
https://brainly.com/question/1360051