a programmer is overloading the equality operator (==) and has created a function named operator==. which of the following statements are true about this function?
Answers
The function named operator== overloads the equality operator (==) in a programming language. It allows the programmer to define custom comparison behavior for objects of a particular class.
When a programmer overloads the equality operator (==) by creating a function named operator==, it allows them to specify custom comparison logic for objects of a specific class. This means that the behavior of the equality operator can be tailored to suit the requirements of the class. By overloading the equality operator, the programmer can define how two objects of the class should be compared for equality. The operator== function typically takes two objects as input and returns a Boolean value indicating whether they are equal or not based on the defined criteria.
This customization enables the programmer to compare objects based on specific attributes or conditions that are meaningful for the class. It provides flexibility in defining equality for complex data structures or user-defined types. It's important to note that overloading the equality operator should follow certain conventions to ensure consistency and avoid unexpected behavior. The overloaded operator should adhere to the principle of equivalence, ensuring that the comparison is reflexive, symmetric, and transitive. Additionally, proper consideration should be given to the type compatibility and possible side effects of the comparison operation.
Learn more about programming language here-
https://brainly.com/question/13563563
#SPJ11
Related Questions
Which option demonstrates when Olga will apply deductive reasoning in the following scenario? Olga is conducting an experiment that compares the spatial reasoning abilities of pigs and dogs.
Olga proposes that pigs will outperform dogs on her spatial reasoning test.
Olga administers a test that allows both pigs and dogs to demonstrate spatial reasoning.
Olga is conducting an experiment that compares the spatial reasoning abilities of pigs and dogs
Olga examines the existing literature concerning spatial reasoning in animals.
Answers
Answer:
i think a
Explanation:
In a(n) _______ sellers post descriptions of products at a website and buyers submit bids electronically.
A)Web auction
B)Spider commerce
C)Digital transaction
D)ActiveX control
Answers
A). Web auction. is the correct option. In a web auction, sellers post descriptions of products on a website and buyers submit bids electronically.
A web auction is a service offered by various internet platforms that allows individuals or businesses to list items or services for sale. Potential buyers can view the listings and place bids, and the highest bidder at the end of the auction wins the item or service.
A web auction has become a popular way of buying and selling products. Web auctions have changed the way people do business. They have expanded the reach of small businesses and made it possible for people to sell goods across borders.
To know more about website visit:
brainly.com/question/13131363
#SPJ11
A folder is one icon considered a short cut true or false
Answers
Answer:
True
Explanation:
A shortcut can be an icon that points to a certain app or website.
Only about 10 percent of the world’s population uses the internet.
A.
True
B.
False
Answers
Because look on our own Brainly there are more than 1,000 people
MARK ME BRAINLEST
Create a module called bigo which has four functions, find1(list, val), find2(list, val), find3(list, val), and find4(list, val). Each of the functions will take as arguments a list followed by a value. The functions will return a boolean as to whether the val is a member of the list.
Answers
All four functions accept a list (lst) and a value (val) as arguments and return a boolean indicating whether the value is present in the list.
I'm glad to help you with your question. Here's the implementation of the "bigo" module with the four required functions:
```python
# bigo.py
def find1(lst, val):
return val in lst
def find2(lst, val):
for item in lst:
if item == val:
return True
return False
def find3(lst, val):
return lst.count(val) > 0
def find4(lst, val):
try:
lst.index(val)
return True
except ValueError:
return False
```
To know more about boolean visit :-
https://brainly.com/question/20709748
#SPJ11
CHOOSE THE CORRECT CONTINUOUS TENSES( PRESENT CONTINUOUS,PAST CONTINUOUS AND FUTURE CONTINUOUS) : 1. I saw a snake while I ____________________ in the forest. am walking was walking will be walking will walk
Answers
Answer:
Explanation:
joe biden>
Which page layout is most commonly used for a website with a large navigation menu?
Answers
Explanation:
The Name is called, (navigation menu..)
to direct users 2 info., they look up...
the stigma of obesity in the general public and its implications for public health–a systematic review.
Answers
The stigma of obesity in the general public refers to the negative attitudes, stereotypes, and discrimination faced by individuals who are overweight or obese. It is a societal bias that often leads to the stigmatization and marginalization of individuals based on their weight.
The implications for public health are significant. The stigma of obesity can have detrimental effects on the physical and mental well-being of individuals. It can contribute to body dissatisfaction, low self-esteem, depression, and anxiety among those who experience weight stigma. Moreover, weight stigma can deter individuals from seeking medical help, engaging in physical activity, or adopting healthy behaviors, leading to poorer health outcomes and increased risks of chronic diseases associated with obesity.
From a public health perspective, addressing weight stigma is crucial for promoting inclusive and equitable health environments. Efforts should focus on raising awareness, promoting education, and challenging societal norms and stereotypes related to body weight. Creating supportive environments that promote body positivity, acceptance, and respect for all individuals, regardless of their weight, can contribute to improved health outcomes and overall well-being. Additionally, healthcare providers should strive to provide non-judgmental and compassionate care to individuals affected by obesity, ensuring that their dignity and rights are upheld.
Learn more about discrimination here
https://brainly.com/question/31315605
#SPJ11
What is a reason given in an argument why the claim is true?
A. Evidence
B. Heuristic
C. Claim
D. Premise
Answers
Answer:
A
Explanation:
A
The reason given in an argument why the claim is true is called; D: Premise.
When having an argument, the parties involved are trying to establish who is right about the topic of the argument based on the claims given by the parties involved in the argument. Now, arguments get to a point where the parties involved would be required to bring forth a string reason why their position holds the best approach or is true and this position as to why their claim is true is called "premise" of the claim in the argument.Read more about arguments at; https://brainly.com/question/3132210
Write any three importance of utility software.
Answers
Answer:
Three importance of Utility Software are:
Utility software is software designed to help to research , configure, optimize or maintain a computer.
It is used to support the pc infrastructure.
Utility Software is used in
System Utilities: Anti-virus utilities scan for PC viruses and block or remove them. File management utilities: Cryptographic utilities encrypt and decrypt streams and files. Storage Management Utilities: Backup software creates copies of entire information stored on a disk and restores either the whole disk (aka Disk cloning) in an occasion of disk failure or marked files that are accidentally deleted or corrupted.
which word pair from list 2 best complete the folowing analogy
Answers
The word pair from list 2 that best complete the analogy is option C= report: describe.
What Constitutes a Good Analogy?A successful analogy strikes a balance between two opposing objectives: recognizability as well as representativeness. The best analogies are well known. They are known to be use as a well-known idea or notion to describe an abstract thought.
Note that an analogy is seen as a form of a verbal word that describes the cognitive act of transferring knowledge or the meaning from one subject to another.
Therefore, The word pair from list 2 that best complete the analogy is option C= report: describe.
Learn more about analogy from
https://brainly.com/question/12010013
#SPJ1

suppose you are writing a jquery command that will display heading elements of the switch class if they are hidden or hide them if they are visible. what should you place in the blank in the following code?
Answers
To display or hide heading elements of the switch class, the toggle() method should be placed in the blank.
The toggle() method is a jQuery method that can be used to display or hide an HTML element. In this case, it can be used to display heading elements of the switch class if they are hidden or hide them if they are visible. The syntax for using the toggle() method is as follows:
$("selector").toggle();
In this syntax, "selector" should be replaced with the CSS selector for the heading elements of the switch class. By using this method, the jQuery command will toggle the visibility of the elements, displaying them if they are hidden, or hiding them if they are visible.
Learn more about jQuery method here;
https://brainly.com/question/32146249
#SPJ11
1.03!! need major help!!
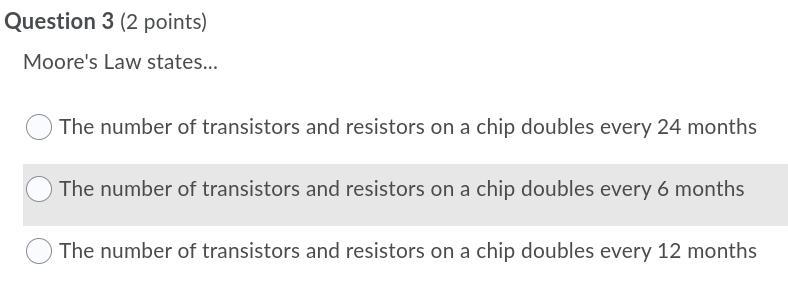
Answers
Answer: the answer is A
Explanation:
Moore's law, prediction made by American engineer Gordon Moore in 1965 that the number of transistors per silicon chip doubles every year. ... Moore observed that the number of transistors on a computer chip was doubling about every 18–24 months.
One example of descriptive text is anchor text, which is:
A) a phrase within tags
B) included within a tag
C) a textual description of a picture
D) highlighted link text, specified inside tags, describing the page to which it links
Answers
One example of descriptive text is anchor text, which is D) highlighted link text, specified inside tags, describing the page to which it links.
Anchor text is the clickable text in a hyperlink that takes the user to another page or resource on the web. It is usually highlighted and underlined in a different color to distinguish it from the rest of the text on the page. The anchor text is specified inside the HTML tags and provides a descriptive and relevant description of the destination page or resource.
For example, if a webpage contains a hyperlink to a blog post about "10 Tips for Effective SEO," the anchor text for the link might be "10 Tips for Effective SEO" or "SEO Tips" rather than a generic phrase like "click here." Using descriptive anchor text can improve the accessibility and usability of a website, as well as help search engines understand the content and context of the linked pages.
Descriptive text is used to provide information and details about a particular topic or subject. It can be used in various forms of communication, such as articles, reports, manuals, and websites. The main purpose of descriptive text is to inform and educate the reader about a particular subject or topic, and to provide them with a clear understanding of the key points and concepts.
Learn more about HTML here:
https://brainly.com/question/17959015
#SPJ4
What is the maximum number of host ip addresses that can exist in a class b network?
Answers
65,534. is the maximum number of host ip addresses that can exist in a class b network.
What two types of IP addresses are utilized on the internet?Every individual or business with an internet service plan will have two types of IP addresses: their private IP addresses and their public IP address. The terms public and personal relate to the network location — that is, a private IP address is used inside a network, while a public one is used outside a network.
What is a class B network?
A Class B network was a network in which all lessons had the two most-significant bits set to 1 and 0 respectively.
For these networks, the network address was given by the next 14 bits of the address, thus departing 16 bits for the numbering host on the network for a total of 65536 lectures per network.
To learn more about IP addresses, refer
https://brainly.com/question/21864346
#SPJ4
Complete Question is,
a. 1022
b. 32,766
c. 8190
d. 65,534.
For each description listed, identify the term that the text best describes.
These are your terms, you can only use one for each question.
Strands, Splice, Termination, Connectors, Shielding, Connection, Reducing Connectors, Grooming, Drain Wire, Amperage Capacity
Here are the questions below.
1. Because of thermal expansion and cold flow of aluminum, standard copper____________ cannot be safely used on aluminum wire.
2. Crimp-type_are used to connect two different sized wires.
3. For fire alarm cable to be effective the_______wire must be grounded.
4. A properly made________should last as long as the insulation on the wire itself.
5. A good electrical________should be mechanically and electrically secure.
6. Typically in instrumentation and control cable only one end is grounded and the ________at the other end is isolated by folding it back and taping over it.
7. Insulation particles can get trapped in the crimp joint and form the basis of a defective______________
8. Poor craftsmanship in stripping and terminations can cause exposed _________,which are a safety hazard.
9. ______________the conductor ensures a proper fit in the crimp barrel.
10. Select the proper size terminal for the wire being terminated, to ensure that the___________ of the lug equals that of the conductor.
Answers
Answer:
1. Termination
2. Connectors
3. Shielding
4. drain wire
5. strands
6. Amperage Capacity
7. Splice
8. Connection
9. Grooming
10. reducing connectors
Explanation:
A shielded cable or screened cable is an electrical cable that has a common conductive layer around its conductors for electromagnetic shielding.
How to Setup My.LoneStar.edu Account?
Answers
To access your My.LoneStar.edu account, enter the LSC ID number that is listed inside the Lone Star College entrance letters that was mailed or emailed to you.
What does test setup mean?Methods for test setup can speed up test execution, especially when dealing with large numbers of records. You may rapidly and effectively create typical test data using test setup methods. You can save time by creating data once for the entire class rather than separately for every test method.
What does setup mean on a car?The race setup, car setup, or vehicle setup in motorsports refers to a group of modifications made to the automobile to enhance its performance, handling, dependability, etc. under particular circumstances.
To know more about setup visit:
brainly.com/question/28117740
#SPJ4
write code to read a list of song durations and song names from input. for each line of input, set the duration and name of newsong. then add newsong to songslist.
Answers
Here's the Python code to read a list of song durations and song names from input and then add them to a songslist:```python songslist = [] while True: try: duration, name = input().split() newsong = {"duration": duration, "name": name} songslist.append(newsong except: break
```In this code, we first create an empty `songslist` list to store the songs. Then, we use a `while` loop to repeatedly read lines of input until there is no more input left (`while True` is an infinite loop, but we break out of it when there is an error reading input).For each line of input, we split it into the duration and name using `input().split()`.
Then, we create a dictionary `newsong` with two keys `"duration"` and `"name"`, and set their values to the duration and name respectively.Finally, we add `newsong` to the `songslist` using the `append()` method.I hope this helps! Let me know if you have any further questions.
To know more about durations visit:
https://brainly.com/question/13567541
#SPJ11
When a specific garment, like the bell-bottom jean, comes into style and then disappears again it's called a ___________. (5 Letters)
Answers
When a specific garment, like the bell-bottom jean, comes into style and then disappears again it's called a fad. A fad is a temporary,
short-lived craze or trend that becomes very popular among a particular group of people within a brief period.
A fad can be a piece of clothing or a way of dressing, hairstyle, a dance, a toy, or even a word or phrase. However, after a while, it loses its popularity, and people move on to something else. Fads can be caused by various factors like media exposure, peer influence, and marketing.
In conclusion, fads are temporary trends or crazes that are popular for a short period and then disappear, making way for a new trend to emerge.
To know more about specific visit:
https://brainly.com/question/27900839
#SPJ11
what is a microphone
Answers
Answer: It is a piece of tech that's used for recording audio
Explanation:
Choose all items that represent examples of good website accessibility.
site easily found using a search engine
font size can be changed
site text makes sense when read aloud to a blind person
pages load quickly
the Tab and Enter keys can be used to move through a website
Answers
Answer:
B,C, E
Explanation:
I did it on edge :)
Answer:
b, c, and e !!
Explanation:
just did the assignment, hope this helps !! <3
brainliest pls? :)
Click to review the online content. Then answer the question(s) below. using complete sentences. Scroll down to view additional
questions.
Memory Matters
Explain the difference between occasional forgetfulness and Alzheimer's disease.
Answers
Answer:
The answer is below
Explanation:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.
Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.
Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Answer:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Explanation:
got 100% on edg
how much u give me from 10


Answers
Answer:
11
Explanation:
Explanation:
10/10 cause you are really cute hehe
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
difference between integrated package and software suite
Answers
Answer:
1) Low cost. It is affordable for the small business.
2) Convenient. An integrated package lets users juggle multiple tasks with similar ease. Switching between the individual applications in an integrated package usually requires a few keystrokes or mouse clicks.
3)Able to share information between modules. As its name implies that integrated packages typically make it easy to transfer, integrated data from one application to another. For example, after making financial calculations in a spreadsheet, we could copy the results directly into a project proposal being written with the word-processing module.
4)Each individual modules generally share a similar command structure. For this reason, procedures learned in one module can be applied to other activities as well.
Explanation:
With most forms of media, you can use up to _____% under “fair use” guidelines.
Answers
Answer:
With most forms of media, you can use up to 10% under “fair use” guidelines.
Why is it a good idea not to change the subject line when replying to a message?
O so that the reply is sent to the original sender
O so that the reply does not bounce back as undeliverable
O so that the reply matches with the sender's original message
O so that the reply does not inadvertently include unintended recipients
Answers
Answer:
C. so that the reply matches with the sender's original message.
Explanation:
The Sender Message Channel Receiver (SMCR) model of communication was developed and created by David Berlo in 1960. SCMR was developed from the Shannon-Weaver model of communication of 1949.
The SCMR model of communication comprises of four (4) main components and these are;
1. Sender (S): this is typically the source of information (message) or the originator of a message that is being sent to a receiver. Thus, they are simply the producer of a message.
2. Channel (C): this is the medium used by the sender for the dissemination or transmission of the message to the recipient. For example, telephone, television, radio, newspapers, billboards etc.
3. Message (M): this is the information or data that is being sent to a recipient by a sender. It could be in the form of a video, audio, text message etc.
4. Receiver (R): this is typically the destination of information (message) or the recipient of a message that is being sent from a sender. Thus, the receiver is any individual who is able to read, hear or see and process the message being sent or communicated in the communication process.
Basically, the communication channel used in SCMR must connect the sender with the desired recipients.
Hence, it is a good idea not to change the subject line when replying to a message, so that the reply matches with the sender's original message.
Answer:
Explanation:
Its C not B
Which two settings must you configure when fortigate is being deployed as a root fortigate in a security fabric topology?
Answers
The two settings that one must configure when fortigate is being deployed as a root fortigate in a security fabric topology are:
Option A. Enables you to view the logical and physical topology of Security Fabric devices.Option C. Enables you to view the security ratings of FortiGate Security Fabric groups.What is security fabric settings?The term Security Fabric is known to be a tool that aids one or allows one's network to be able to automatically see and also dynamically isolate any kinds of affected devices.
Note that is one that can also partition network segments, update rules, and they can bring out new policies, and delete malware.
Hence, The two settings that one must configure when fortigate is being deployed as a root fortigate in a security fabric topology are:
Option A. Enables you to view the logical and physical topology of Security Fabric devicesOption C. Enables you to view the security ratings of FortiGate Security Fabric groups.See full question below
Which two Security Fabric features are on FortiManager? (Choose two.)
Select one or more:
A. Enables you to view the logical and physical topology of Security Fabric devices
B. Enables you to run security rating on FortiGate devices
C. Enables you to view the security ratings of FortiGate Security Fabric groups
D. Enables you to view and renew Security Fabric licenses for FortiGate devices
Learn more about security from
https://brainly.com/question/25720881
#SPJ1
Which is an attribute to look for when choosing the proper plugin for specialized envelope/ADSR compression techniques?
Answers
When choosing a plugin for specialized envelope/ADSR compression techniques, an important attribute to look for is the ability to customize the envelope settings.
This includes options for adjusting attack, decay, sustain, and release times, as well as the ability to shape the envelope curves. Additionally, it is important to choose a plugin that offers advanced compression techniques such as side chain compression and parallel compression to achieve the desired effect.
ADSR stands for Attack, Decay, Sustain, and Release, which are the four stages of a sound's envelope. Envelope control allows you to adjust the level and duration of each stage of the envelope, which can be useful for shaping the dynamics and timbre of a sound in a more detailed and nuanced way.
For more information about envelope/ADSR, visit:
https://brainly.com/question/28968801
#SPJ11
Describe how keeping the antivirus software up to date and reduces the risks of viruses on the computer.
Answers
The anti-virus updates contain the latest files needed to combat new viruses and protect your computer. Antivirus software provides signature files which are very important since they contain the latest lists of known viruses. These signature files are released daily, and sometimes even more often