a person wants to transmit an audio file from a device to a second device. which of the following scenarios best demonstrates the use of lossless compression of the original file?
Answers
In the scenario where a person wants to transmit an audio file from one device to another, using lossless compression would be the best option to maintain the original quality of the audio.
Lossless compression reduces the file size without losing any data or affecting the audio quality, ensuring that the recipient receives the exact same audio as the sender. This is particularly useful for applications where high-fidelity audio is essential, such as professional music production or critical communication. In this case, the person would compress the original file using a lossless format like FLAC or ALAC before transmitting it to the second device, resulting in efficient transmission without sacrificing audio quality.
Learn more about Lossless compression here:
https://brainly.com/question/20087556
#SPJ11
Related Questions
open accomplishing your task I was able to
Answers
Answer:
WTH KINDA QUESTION IS THIS !
I DON'T UNDERSTAND DUDE
_____ is the feature that allows you to quickly advance cell data while filling a range of cells.
A. Auto Fill
B. AutoCopy
C. FillAuto
D. CopyAuto
Please no files just type the answer, thanks!
Answers
Answer:
A. Auto Fill
Explanation:
Auto Fill is the feature that allows you to quickly advance cell data while filling a range of cells.
Choose the best answer to complete the sentence.
A transferable skill can be applied:
in a variety of situations and roles.
in only one setting or situation.
in every situation.
Answers
Answer:
First is A
Explanation:
Second is B,C,F
For windows xp, 2000, and nt servers and workstations, raid 0 or ____ is available.
Answers
For windows XP, 2000, and NT servers and workstations, raid 0 or 1 is available.
What is NT in network?NT's technology is known to be a type of tech that is said to be the base for any form of Microsoft successor operating system, that is Windows 2000.
Note that Windows NT which is "New Technology," is known to be made up of two products: Microsoft NT Workstation as well as Microsoft NT Server.
Therefore, For windows XP, 2000, and NT servers and workstations, raid 0 or 1 is available.
Learn more about servers from
https://brainly.com/question/15498455
#SPJ1
George is a contractor who creates websites and web applications. What is George working as?
Answers
Answer:
Web developers
Explanation:
Web developers are responsible for designing and developing websites and website applications.
cassie is an it help desk representative. she just received a trouble ticket from a remote user stating they cannot connect to the company network over the virtual private network (vpn). cassie begins troubleshooting the matter, checking on recent configuration changes to the vpn equipment, looking at the unit's logs for error messages, and so on. she has examined the vpn-related features and potential problems but still doesn't understand why the end user's connection failed. she has been assured that both the end user and the company have internet connectivity. what is the most likely reason the user cannot connect?
Answers
A network engineer has inadvertently changed the IP address of the firewall's internal interface that connects to the VPN's outward- facing port.
What is an IP address?A computer network that employs the Internet Protocol for communication will have an IP address, which is a numerical label.Network interface identification and location addressing are the two primary purposes of an IP address. The Internet Assigned Numbers Authority (IANA) and five regional Internet registries (RIRs) are in charge of managing the IP address space on a global scale .They are in charge of assigning IP addresses to local Internet registries, such as Internet service providers (ISPs) and other end users, in their respective regions. IANA allocated IPv4 addresses to the RIRs in blocks of roughly 16.8 million addresses each, but IANA has run out of IPv4 addresses as of 2011. For local assignments in Africa, just one RIR still has a supply.To learn more about network, refer:
https://brainly.com/question/1167985
#SPJ4
Discuss, in your own words, the topic of cybersecurity management for both individuals and business. Briefly talk about the different threats, and then explain what cybersecurity management is, and what it could do against each common type of threat.
Answers
Cybersecurity management protects individuals and businesses from threats.
How does cybersecurity management safeguard individuals and businesses?Cybersecurity management is essential for both individuals and businesses to protect themselves from the ever-increasing threats in the digital landscape. In today's interconnected world, individuals face various cybersecurity risks, such as malware, phishing attacks, identity theft, and data breaches.
Similarly, businesses are vulnerable to targeted attacks, ransomware, insider threats, and intellectual property theft.
Cybersecurity management involves implementing proactive measures to prevent and mitigate these threats. It includes the use of robust security tools, regular software updates, strong passwords, and user awareness training.
Additionally, businesses should employ network monitoring, intrusion detection systems, and incident response plans to detect and respond to any security breaches promptly.
How cybersecurity management works by adopting a layered defense approach, combining technology, policies, and employee awareness. A comprehensive strategy should include firewalls, antivirus software, encryption, multi-factor authentication, and regular data backups.
It is crucial to continually assess and update security measures to stay ahead of evolving threats and ensure a secure digital environment.
Learn more about Cybersecurity
brainly.com/question/30902483
#SPJ11
Apple Inc.: Prior to the company's 2017 move to Apple Park, on what street in Cupertino was Apple's headquarters located? It shares a name with a construct that mischievous young programmers may have learned by typing the following into the BASIC prompt on an Apple ][:
10 PRINT "BUTTS "
20 GOTO 10?
Answers
According to the question of programmers, apple's headquarters was located on Infinite Loop in Cupertino.
What is programmers?Programmers are professionals who write code to create software programs, applications, and websites. They use programming languages to instruct computers to perform specific tasks. Programmers analyze user needs and develop software solutions. They also design, test, and debug software, as well as perform maintenance and upgrades. Programmers use problem-solving and analytical skills to design and develop software that meets user needs. They must stay up-to-date on the latest technology and programming languages to create the most efficient and effective solutions. Programmers must also be able to understand customer requirements and develop a plan to meet those needs.
To learn more about programmers
https://brainly.com/question/30168154
#SPJ1
Which process refers to starting up a computer?
Is the process of starting a computer.
Reset
Next
Answers
Wheeler at the Federal Communications Commission (FCC) has a huge pile of requests from radio stations in the Continental U.S. to transmit on radio frequency 88.1 FM. The FCC is happy to grant all the requests, provided that no two of the requesting locations are within Euclidean distance 1 of each other (distance 1 might mean, say, 20 miles). However, if any are within distance 1, Prof. Wheeler will get annoyed and reject the entire set of requests. Suppose that each request for frequency 88.1 FM consists of some identifying information plus (x, y) coordinates of the station location. Assume that no two requests have the same x coordinate, and likewise no two have the same y coordinate. The input includes two sorted lists, Lx of the requests sorted by x coordinate and Ly of the requests sorted by y coordinate.
(a) Suppose that the map is divided into a square grid, where each square has dimensions 1x7. Why must the FCC reject the set of requests if two requests are in, or on the boundary of, the same square?
(b) Design an efficient algorithm for the FCC to determine whether the pile of requests contains two that are within Euclidean distance 1 of each other; if so, the algorithm should also return an example pair. For full credit, your algorithm should run in O(n lg n) time, where n is the number of requests. Hint: Use divide-and-conquer, and use Part (a).
(c) Describe how to modify your solution for Part (b) to determine whether there are three requests, all within distance 1 of each other. For full credit, your algorithm should run in O(n lg n) time, where n is the number of requests.
Answers
An efficient algorithm using divide-and-conquer: sort requests by x and y coordinates, recursively split by x-coordinate, find closest pairs in halves, determine the minimum distance, create a new list within the x-range, iterate through points and calculate distances to find closest pair.
How can an algorithm using divide-and-conquer efficiently determine if there are two requests within a Euclidean distance of 1 from each other, and how can it be modified to determine if there are three requests within distance 1?If two requests are in or on the boundary of the same square in the grid, it means their x and y coordinates fall within the same range of values, which is 1x7. Since the Euclidean distance between two points is calculated based on their coordinates, if two requests are in the same square, their Euclidean distance will be less than or equal to 1.
Thus, the FCC must reject the set of requests to ensure that no two stations are within a distance of 1 from each other.
To design an efficient algorithm to determine if there are two requests within a Euclidean distance of 1 from each other, we can utilize a divide-and-conquer approach. The algorithm can follow these steps:
Sort the list of requests by x-coordinate, resulting in Lx.
Sort the list of requests by y-coordinate, resulting in Ly.
Define a helper function, closestPair(Lx, Ly), which takes the sorted lists Lx and Ly as input.
If the length of Lx is less than or equal to 3, calculate and return the closest pair among those requests using a brute-force approach.
Divide Lx into two halves, Lx_left and Lx_right, split evenly.
Determine the midpoint, mid_x, between the x-coordinates of the rightmost point in Lx_left and the leftmost point in Lx_right.
Create two new lists, Ly_left and Ly_right, containing the requests from Ly that fall within the range (mid_x - 1, mid_x + 1).
Recursively call closestPair(Lx_left, Ly_left) and closestPair(Lx_right, Ly_right) to find the closest pairs within each half.
Determine the minimum distance, d, among the closest pairs from the previous step.
Create a new list, Sy, containing the requests from Ly that fall within the range (mid_x - d, mid_x + d).
Iterate through each point in Sy, considering only the points whose y-coordinate is within d of the current point's y-coordinate.
Calculate the distance between each pair of selected points, keeping track of the minimum distance found.
Return the closest pair found in the entire process.
The runtime complexity of this algorithm is O(n log n) because the recursive calls split the problem in half and the merging step takes O(n) time.
To modify the algorithm for Part (b) to determine if there are three requests within a distance of 1 from each other, we can make the following changes:
After finding the closest pair in each half of the recursion, determine the minimum distance, d, among the closest pairs.
Create a new list, Sy, containing the requests from Ly that fall within the range (mid_x - d, mid_x + d).
Sort the list Sy by y-coordinate.
Iterate through each point in Sy, considering only the points whose y-coordinate is within d of the current point's y-coordinate.
For each selected point, iterate through the next six points (or fewer if fewer than six points remain) and calculate the distance between each pair of points.
If any calculated distance is less than or equal to 1, return the three points forming that pair.
If no three points within distance 1 are found, return that there are no three requests within distance 1.
The runtime complexity of this modified algorithm is still O(n log n) because the additional steps introduced in Part (c) do not affect the overall complexity.
Learn more about algorithm
brainly.com/question/31936515
#SPJ11
The terminology used to describe a possible path to resolution to a problem from one end to the other is called what?
Answers
The terminology used to describe a possible path to a resolution to a problem from one end to the other is called a solution.
What is terminology?The research of these phrases and related applications is known as terminology science. A glossary is a collection of specialist words plus their corresponding interpretations in a given field.
If there is a body or a term which is the need to have a resolution that needs to be made through that the person can evaluate and find a solution for the following situation then that is called a resolution or solution for that particular problem
Learn more about terminology, here:
https://brainly.com/question/2511894
#SPJ1
Reimplement the Bug class from the preceding exercise, but use a different internal representation. Represent the distance climbed by a string of - characters, one for every 10 cm. The up and getPosition methods should have the exact same behavior as before. Of course, their implementation will be quite different.
Answers
By representing the distance climbed using a string of "-" characters, we can easily visualize the distance in increments of 10 cm. The `up` and `getPosition` methods have the same behavior as before, but their implementation is different.
To reimplement the Bug class using a different internal representation, we can represent the distance climbed by a string of "-" characters, where each "-" represents 10 cm. Here is the revised code:
```
public class Bug {
private int position;
private String distance;
// Constructor
public Bug() {
position = 0;
distance = "";
}
// Move the bug up by 10 cm
public void up() {
position += 10;
distance += "-";
}
// Get the bug's current position
public int getPosition() {
return position;
}
// Get the bug's distance climbed
public String getDistance() {
return distance;
}
// Main method
public static void main(String[] args) {
Bug bug = new Bug();
bug.up(); // Move the bug up by 10 cm
bug.up(); // Move the bug up by another 10 cm
System.out.println("Bug's position: " + bug.getPosition());
System.out.println("Bug's distance climbed: " + bug.getDistance());
}
}
```
Explanation:
1. We have added a new instance variable `distance` of type String to represent the distance climbed.
2. In the constructor, we initialize the `position` to 0 and `distance` to an empty string.
3. In the `up` method, we increment the `position` by 10 and concatenate a "-" to the `distance` string.
4. The `getPosition` method returns the current position of the bug.
5. The `getDistance` method returns the string representation of the distance climbed.
6. In the `main` method, we create an instance of the Bug class and call the `up` method twice to move the bug up by 10 cm each time.
7. Finally, we print the bug's position and the distance climbed.
Conclusion:
By representing the distance climbed using a string of "-" characters, we can easily visualize the distance in increments of 10 cm. The `up` and `getPosition` methods have the same behavior as before, but their implementation is different.
To know more about string visit
https://brainly.com/question/946868
#SPJ11
For a horror film, Pauline wants to show a computer-generated monster appearing from the body of an actor. How can she do this?
A. use a green screen and film the actor then add the animated monster using the green screen
B. make the actor wear a green patch on his chest then add the animated monster on the green patch
C. make the scene of the actor opaque and add the scene of the monster as the bottom track
D. tween the actor and the animated head using a tweening software
E. film the head on a green screen and then add the actor to the background
Answers
the answer is option D
Explanation:
Alpha Technologies, a newly established company, wants to share information about its work with people all over the world. Which type of server should this company use to upload their information?
Answers
This answer from the pro IdowShadow
Option A, Web Server, because it is a type of HTTP server used to direct web pages and blogs, as a method of transmitting information through a web platform for personal or business use, to publicize a business or an organization.
A good customer service representative develops qualities that make the
customer feel satisfied and valued such as the ability to listen.
True
False
Answers
Answer:
true
Explanation: if this is not the answer sorry for get it wrong
7.3.4: Find the Error
Answers
Answer:
my_string = "hello!"
# One of the two lines below will cause an error.
# Each line is an attempt to replace the first
# letter of myString with H. Comment out the
# line you think is incorrect.
# my_string[0] = "H"
my_string = "H" + my_string[1:]
print(my_string)
Explanation:
The numeric or alphanumeric error code is being used to identify the type of error. Following are the description of the error code in the given question:
Incorrect code:
my_string[0] = "H" // this line give the error that is "'str' object does not support item assignment".
Correct code:
my_string = "hello!"#defining the string variable that is "my_string"
my_string = "H" + my_string[1:]#using string variable that perform slicing and hold its value
print(my_string)#print my_string value
Code Explanation:
Defining the string variable that is "my_string".In the next line, the string variable is used that adds "H" to the first index value and performs slicing, and holds its value. Using the print method that prints the "my_string" variable value.Output:
Please find the attached file.
Find out more about the error here:
brainly.com/question/13106116


the tthe type of cable that is most likely to be used for medium-powered, network-powered broadband communication in a vertical shaft space is?ype of cable that is most likely to be used for medium-powered, network-powered broadband communication in a vertical shaft space is?
Answers
Powered broadband communication in a vertical shaft space is BMR.
What is vertical shaft?
A shaft that is lowered directly downward or at a 90-degree angle with the horizon in order to reach the planet's center.
What is BMR?
An average man has a BMR of around 7,100 kJ per day, while an average woman has a BMR of around 5,900 kJ per day. Energy expenditure is continuous, but the rate varies throughout the day. The rate of energy expenditure is usually lowest in the early morning.
Broadband, which is used in fast internet connections, is wide bandwidth data transmission that carries multiple signals at a variety of frequencies and Internet traffic types. This allows messages to be sent simultaneously. The media can be twisted pair, satellite, wireless Internet (radio), optical fiber, coaxial cable, or optical fiber.
Many computer networks employ a straightforward line code to send one kind of signal throughout the entire baseband bandwidth of the channel (from zero through the highest frequency needed). Most iterations of the widely used Ethernet family have names to denote this, such as the original from the 1980s.
Broadband refers to the wide range of frequencies that may support both many data users and conventional television channels on the same cable in networks that employ cable modems on normal cable television infrastructure. For each band in a broadband system, a distinct radio frequency modulated by the data signal is often used.
Learn more about broadband cable click here:
https://brainly.com/question/19538224
#SPJ4
If a packet gets "sucked down a black hole" (figuratively speaking) and is not received by its sender, and no message is sent back explaining the situation, then something is wrong. The failure to send a message means something is wrong with the _____. ICMP
ISO
TCP/IP
HTTP.
Answers
The failure to send a message implies that something is wrong with the ICMP.
What is ICMP in computer networks?ICMP is a term that means Internet Control Message Protocol. It is regarded as a kind of error-reporting protocol or method of network devices.
It can be seen in routers as they are often use to get error messages to the source IP address if their network problems hinders them in terms of delivery of IP packets. The failure to send a message shows that something is wrong with the ICMP.
Learn more about ICMP from
https://brainly.com/question/9473592
Consider the following code segment.
int[][] mat = {{10, 15, 20, 25},
{30, 35, 40, 45},
{50, 55, 60, 65}};
for (int[] row : mat)
{
for (int j = 0; j < row.length; j += 2)
{
System.out.print(row[j] + " ");
}
System.out.println();
}
What, if anything, is printed as a result of executing the code segment?
A 10 15 20 25
50 55 60 65
B 10 20
30 40
50 60
C 10 15 20 35
30 35 40 45
50 55 60 65
D Nothing is printed, because an ArrayIndexOutOfBoundsException is thrown.
E Nothing is printed, because it is not possible to use an enhanced for loop on a two-
dimensional array.
Answers
Answer:
C
Explanation:
10 15 20 35
30 35 40 45
50 55 60 65
How do I make the text and heading different colors?
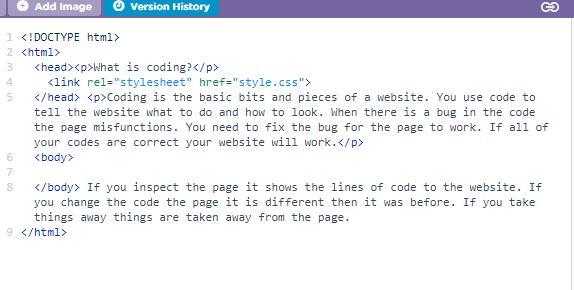
Answers
Answer: do u have word if you do go to font and u can change ur font
Explanation:
why is this not working out? I'm confused I thought that because it was a "guess.isdigit()" it would only continue if i was a number??


Answers
Answer:
Because guess is not converted to int
Explanation:
try adding line "guess = int(guess)" between lines "if guess.isdigit():" and "print("That's Correct!")"
This is because input() returns data of type string. Arithmetic operations cannot be performed between different types. Just replace the first line with this and your problem will be solved.
guess = int(input("Guess a number between 1 and 10: "))we cannot share software in computer network true or false
Answers
Answer:
false
Explanation:
false but other thing is that it can be very risky increasing the chances of getting infected by a virus
you need to create a domain-based namespace on a windows server 2016 server in the westsim domain. which of the following is true concerning this type of namespace? (select two.)
Answers
When creating a domain-based namespace on a Windows Server 2016 server in the Westsim domain, the following are true:
1. It allows for centralized management of the namespace.
2. It can provide access-based enumerationExplanation:
To create a domain-based namespace on a Windows Server 2016 server in the Westsim domain, it is essential to know that a domain-based namespace allows for centralized management of the namespace and it can provide access-based enumeration.
A namespace in computer networks is a collection of nodes that are uniquely named and can be referenced to create an identifiable system. A namespace may refer to a single node or to a collection of nodes that work together. Namespaces are generally used in programming or computer networking to define unique names for different objects, such as servers, databases, or applications.
The creation of a domain-based namespace on a Windows Server 2016 server in the Westsim domain has the following advantages: Centralized management of namespace: This implies that you can create, configure, and manage a namespace using a single tool on a central server. It provides the necessary framework for organizing and naming your data in a way that makes sense for your organization. Access-based enumeration: It is a feature that hides data from users who do not have permission to access it. It ensures that users can only see files and folders they have access.
Learn more about windows:
https://brainly.com/question/1594289
#SPJ11
Write a program that meets the following requirements: - Creates an array with size 5 and prompts the user to enter five integers. - Should prompt the user to input the number again if the input is incorrect (you can catch InputMismatchException or NumberFormatException). - Once the array is ready, prompt the user to enter the two indexes of the array, then display the sum of the corresponding element values. If any of the specified indexes are out of bounds, you can catch ArrayIndexOutOfBoundsException or IllegalArgumentException and display the message "Out of Bounds". Ask new input to make sure that system doesn't fail if invalid input is provided. Sample Run: Input five integers: 29 a 2687 Incorrect input! Try again. Input five integers: 29502687 Input two indexes: 05 Out of Bounds! Try again. Input two indexes: 01 The sum of 29 and 50 is 79.
Answers
Here is a Java program
```
import java.util.Scanner;
public class Main {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
int[ ] nums = new int[5];
System.out.println("Input five integers: ");
for (int i = 0; i < nums.length; i++) {
try {
nums[i] = input.nextInt();
} catch (Exception e) {
System.out.println("Incorrect input! Try again.");
i--;
input.next();
}
}
int index1, index2;
while (true) {
try {
System.out.print("Input two indexes: ");
index1 = input.nextInt();
index2 = input.nextInt();
if (index1 < 0 || index1 >= nums.length ) {
throw new ArrayIndexOutOfBoundsException();
}
if(index2 < 0 || index2 >= nums.length ){
throw new ArrayIndexOutOfBoundsException();
}
break;
} catch (ArrayIndexOutOfBoundsException e) {
System.out.println("Out of Bounds! Try again.");
}
}
System.out.println("The sum of " + nums[index1] + " and " + nums[index2] + " is " + (nums[index1] + nums[index2]));
}
}
```
In this program, we first create an integer array of size 5 and prompt the user to enter five integers. We use a try-catch block to catch InputMismatchException in case the user enters a non-integer input. If an incorrect input is entered, we display an error message and ask the user to input the number again.
Once the array is ready, we use another try-catch block to catch ArrayIndexOutOfBoundsException. We prompt the user to enter two indexes and check if they are within the bounds of the array. If any of the specified indexes are out of bounds, we throw an ArrayIndexOutOfBoundsException and display an error message. We ask the user to input the indexes again until they are within the bounds of the array.
Finally, we display the sum of the corresponding element values for the specified indexes.
Learn more about Exception handling : https://brainly.com/question/30693585
#SPJ11
Pedro needs to write a block of code that will repeat a loop six times. Which type of loop should he use?
O for
O else
O else if
O while
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
Petro needs to write a block of code that repeats six times. The given options in this question that what should he use to implement the six times a block of code are:
for else else if whileThe correct option to this question is: 1 -for-loop.
So, Pedro needs to use for-loop to write a block of code that will repeat a loop six times. Because when you use for-loop, you know how many iterations are in a loop to execute a block of code. So in this case, the number of iteration is known. Therefore, Pedro needs to use for-loop.
While other options are not correct because:
Else and else are used to make decisions, these are not used to repeat a block of code. These are code branching statements in simple words. While while-loop is used to iterate/loop a block of code but when you don't know the exact number of repetitions.
Answer:
for loop
Explanation:
sorry im late
How long does it take to load in customers and a starting balance from a previous business management software?
Answers
It is difficult to provide a specific time estimate for loading in customers and a starting balance, as it will vary based on these factors. However, most modern software should be able to complete the task in a reasonable amount of time.
The time to load in customers and a starting balanceFirstly, the size of the customer database and the amount of data associated with each customer can impact the loading time. Similarly, the complexity and volume of financial data in the starting balance will affect the loading time.
The speed and processing power of the computer being used also play a role in the loading time.
Generally, newer and more powerful computers will be able to handle larger data sets more quickly. In addition, the software being used to load in the customers and starting balance can impact the loading time.
Some software may be optimized for faster data importing, while others may require more time to process the data.
Learn more about management software at
https://brainly.com/question/31667018
#SPJ11
6. Python indexes lists beginning with the number 1.
True
False
Answers
Answer:
True
Explanation:
Python is like coding
Stephen has been instructed to update all three routers' firmware for his organization. where should he document his work?
Answers
As Stephen has been instructed to update all three routers' firmware for his organization, the change management system is where he should document his work.
What is a change management system?The system involves a process that is responsible for managing all changes to the production operations environment from inception to completion.
The system of change management plays a major role in transforming a client business into a data-driven, intelligent enterprise in data culture and literacy.
Therefore, the change management system is where Stephen should document his work.
Read more about change management system
brainly.com/question/24268860
#SPJ1
can someone tell me what to do i’m kinda stuck and don’t know what he’s telling me to do pls ill give brainlist and points

Answers
Answer:
Well a debtor is basically someone owing someone money, basically someone in debt. He’s telling cup head boy to take care of the people who owe him or someone else their or his money. Thats basically it.
What are limitations of AI
Answers
Explanation:
Limitations of artificial intelligence. One of the main barriers to implementing AI is the availability of data. Data is often siloed or inconsistent and of poor quality, all of which presents challenges for businesses looking to create value from AI at scale.
Answer:
Risks and limitations of artificial intelligence in business
Businesses are increasingly looking for ways to put artificial intelligence (AI) technologies to work to improve their productivity, profitability and business results.
However, while there are many business benefits of artificial intelligence, there are also certain barriers and disadvantages to keep in mind.
Limitations of artificial intelligence
One of the main barriers to implementing AI is the availability of data. Data is often siloed or inconsistent and of poor quality, all of which presents challenges for businesses looking to create value from AI at scale. To overcome this, you should have a clear strategy from the outset for sourcing the data that your AI will require.
Another key roadblock to AI adoption is the skills shortage and the availability of technical staff with the experience and training necessary to effectively deploy and operate AI solutions. Research suggests experienced data scientists are in short supply as are other specialised data professionals skilled in machine learning, training good models, etc.
Cost is another key consideration with procuring AI technologies. Businesses that lack in-house skills or are unfamiliar with AI often have to outsource, which is where challenges of cost and maintenance come in. Due to their complex nature, smart technologies can be expensive and you can incur further costs for repair and ongoing maintenance. The computational cost for training data models etc can also be an additional expense.
Software programs need regular upgrading to adapt to the changing business environment and, in case of breakdown, present a risk of losing code or important data. Restoring this is often time-consuming and costly. However, this risk is no greater with AI than with other software development. Provided that the system is designed well and that those procuring AI understand their requirements and options, these risks can be mitigated.
See also Industry 4.0 challenges and risks.
Other AI limitations relate to:
implementation times, which may be lengthy depending on what you are trying to implement
integration challenges and lack of understanding of the state-of-the-art systems
usability and interoperability with other systems and platforms
If you're deciding whether to take on AI-driven technology, you should also consider:
customer privacy
potential lack of transparency
technological complexity
If you're considering writing a tender document to procure AI, you can seek help from the Northern Ireland Artificial Intelligence Collaborative Network(link is external).
AI and ethical concerns
With the rapid development of AI, a number of ethical issues have cropped up. These include:
the potential of automation technology to give rise to job losses
the need to redeploy or retrain employees to keep them in jobs
fair distribution of wealth created by machines
the effect of machine interaction on human behaviour and attention
the need to address algorithmic bias originating from human bias in the data
the security of AI systems (eg autonomous weapons) that can potentially cause damage
the need to mitigate against unintended consequences, as smart machines are thought to learn and develop independently
While you can't ignore these risks, it is worth keeping in mind that advances in AI can - for the most part - create better business and better lives for everyone. If implemented responsibly, artificial intelligence has immense and beneficial potential.