A misplacement of punctuation or spacing in a command during programming that causes the program to stop running is most
likely which type of error?
syntax
run-time
logic
compiler
Answers
Answer:
Hello!
The answer is
A. SyntaxExplanation:
syntax errors are due to misuse of the proper syntax in the programming language.
(idk if my explanation helps, but it's Syntax.)
Hope this helps!
A misplacement of punctuation or spacing in a command during programming that causes the program to stop running is most likely a: A. syntax error.
What is a syntax error?A syntax error can be defined as a type of error that typically occurs due to mistakes in the source code of a program such as:
Spelling of words.Punctuation errorsIncorrect labelsSpacingIn conclusion, a misplacement of punctuation or spacing in a command during programming that causes the source code of a program to stop running is most likely a syntax error.
Read more on computer codes here: brainly.com/question/25619349
#SPJ2
Related Questions
calculate amat if it is known that on average, 80% of l1 cache access latency is overlapped with computation, 40% of l2 cache access latency is overlapped with computation and 10% of l2 miss latency is overlapped with computation. assume that on average, 3 memory references are serviced simultaneously for l1 cache accesses, 2.5 memory references are serviced simultaneously for l2 cache accesses, and only 1.5 for l2 cache misses ?
Answers
The Average Memory Access Time (AMAT) is approximately 15.77 nanoseconds.
The calculation of AMAT (Average Memory Access Time) involves considering the different latencies and their overlapping percentages for the L1 cache, L2 cache, and L2 cache misses. Let's calculate AMAT step-by-step using the given information:
1. Calculate the effective L1 cache access time:
- Since 80% of L1 cache access latency is overlapped with computation, we can assume that 20% of the access time is not overlapped.
- If we consider 3 memory references serviced simultaneously, then the effective L1 cache access time would be 20% of the total access time divided by 3. For example, if the total L1 cache access time is 100 nanoseconds, the effective L1 cache access time would be (20/100) * 100 / 3 = 6.67 nanoseconds.
2. Calculate the effective L2 cache access time:
- With 40% of L2 cache access latency overlapped with computation, we can assume that 60% of the access time is not overlapped.
- If we consider 2.5 memory references serviced simultaneously, then the effective L2 cache access time would be 60% of the total access time divided by 2.5. For example, if the total L2 cache access time is 200 nanoseconds, the effective L2 cache access time would be (60/100) * 200 / 2.5 = 48 nanoseconds.
3. Calculate the effective L2 cache miss latency:
- Considering that only 10% of L2 cache miss latency is overlapped with computation, we can assume that 90% of the miss latency is not overlapped.
- If we consider 1.5 memory references serviced simultaneously, then the effective L2 cache miss latency would be 90% of the total miss latency divided by 1.5. For example, if the total L2 cache miss latency is 500 nanoseconds, the effective L2 cache miss latency would be (90/100) * 500 / 1.5 = 300 nanoseconds.
4. Calculate AMAT:
- AMAT is calculated as the sum of the product of access probability and access time for each cache level.
- Let's assume the probabilities of accessing L1, L2, and L2 cache misses are P1, P2, and Pmiss respectively.
- If we know that P1 = 0.9 (90% of memory references access L1 cache), P2 = 0.08 (8% of memory references access L2 cache), and Pmiss = 0.02 (2% of memory references result in L2 cache misses), we can calculate AMAT using the formula:
AMAT = P1 * (effective L1 cache access time) + P2 * (effective L2 cache access time) + Pmiss * (effective L2 cache miss latency)
- Using the values calculated earlier, the AMAT would be:
AMAT = 0.9 * 6.67 + 0.08 * 48 + 0.02 * 300 = 5.93 + 3.84 + 6 = 15.77 nanoseconds.
Therefore, the Average Memory Access Time (AMAT) is approximately 15.77 nanoseconds.
To know more about AMAT visit:
https://brainly.com/question/31817396
#SPJ11
you have written a program that runs for exactly 100 minutes when run serially. 4% of the code's serial execution time is spent in code that cannot be parallelized. the remaining portions of code have been parallelized to run concurrently. if we were to execute the program using 8 threads, what would the wall-clock time for our program be in minutes?
Answers
If 4% of the code's serial execution time cannot be parallelized, then the remaining 96% of the code can be parallelized to run concurrently.
Using 8 threads, we can divide the workload evenly and reduce the execution time. The total parallel execution time would be 96% divided by 8 threads, which is 12%. Therefore, the total parallel execution time would be 12 minutes. Adding the non-parallelizable code, the total wall-clock time for the program would be 12 minutes + 4 minutes = 16 minutes. So if we were to execute the using 8 threads, the wall-clock time for our program would be 16 minutes.
To know more about threads visit:
brainly.com/question/28289941
#SPJ11
what dose 34345443454343434344533778876866787689983qw3ww334w54e54343454543434354354354e4554345354345334454335353555334453453434343434343543543543453454353535445354534534555453453435434535434535434354345354345343434344343434444w33334w43w43w43w3w3w4345676747627647567465675664365635636574869817867901123456789098765432234567899876456787655435654354345634343434343 +476567756687865
Answers
3434544345434343434453377887686678768998333345454343454543434354354354455434535434533445433535355533445345343434343434354354354345345435353544535453453455545345343543453543453543435434535434534343434434343444433334434343334345676747627647567465675664365635636574869817867901123456789098765432234567899876456787655435654354345634343434343 + 476567756687865 = 3434544345434343434453377887686678768998333345454343454543434354354354455434535434533445433535355533445345343434343434354354354345345435353544535453453455545345343543453543453543435434535434534343434434343444433334434343334345676747627647567465675664365635636574869817867901123456789098765432234567899876456787655435654354.8222021e+15
Didn't expect that didn't you.
18
A drawback of the project management software is
that it does not have the capacity to calculate the critical path(s) for a project
Group of answer choices
o True
o False
Answers
The given statement “18A drawback of the project management software is that it does not have the capacity to calculate the critical path(s) for a project” is false.
In fact, one of the benefits of project management software is that it is equipped to calculate critical paths.
Critical path analysis (CPA) is a crucial part of project management. It is the process of identifying the longest sequence of tasks in a project that must be completed on time to meet the project’s deadlines.
CPA determines the minimum amount of time required to complete a project and helps to identify which activities can be delayed without affecting the overall timeline of the project.Project management software usually has the ability to perform critical path analysis and display the results in a Gantt chart or network diagram.
The software is programmed to identify the critical path(s) and highlight the activities that are critical to the project's timeline. This information can help project managers to make informed decisions about how to allocate resources, prioritize tasks, and manage risks in order to ensure that the project is completed on time and within budget.
In conclusion, project management software is not limited in its ability to calculate critical paths. In fact, it is a key feature of most project management software and is essential to effective project planning and management.
For more such questions on project management software, click on:
https://brainly.com/question/29646049
#SPJ8
A turbojet is flying with a velocity of 320m/s at an altitude of 9150m, where the ambient conditions are 32kPa and −
32
o
C
. The pressure ratio across the compressor is 12, and the temperature at the turbine inlet is 1400K. Air enters the compressor at a rate of 40Kg/s, and the jet fuel has a heating value of 42,700 kJ/kg. Assuming ideal operation for all components and constant specific heats for air at room temperature, determine:
(a) the temperature (K) and pressure (kPa) at the turbine exit,
(b) Draw a T-s diagram
(c) the velocity of the exhaust gases,
(d) the propulsive power developed in kW,
(e) the propulsive efficiency
(f) the rate of fuel consumption in kg/s.
Answers
(a) The temperature at the turbine exit is 1293 K and the pressure is 38.6 kPa.
(b) Please refer to the attached T-s diagram.
(c) The velocity of the exhaust gases is 871.2 m/s.
(d) The propulsive power developed is 576.4 kW.
(e) The propulsive efficiency is 44.9%.
(f) The rate of fuel consumption is 9.36 kg/s.
(a) The temperature and pressure at the turbine exit can be determined using the equations for an isentropic process, which are:
T2 = T1 * (P2 / P1)^((gamma - 1) / gamma)
P2 = P1 * (T2 / T1)^(gamma / (gamma - 1))
T2 = 1400K * (1 / 12)^((1.4 - 1) / 1.4) = 882.6K
P2 = 32kPa * (882.6K / 1400K)^(1.4 / (1.4 - 1)) = 2.67kPa
Therefore, the temperature at the turbine exit is 882.6K and the pressure is 2.67kPa.
(c) The velocity of the exhaust gases can be determined using the equation for the velocity of a gas in an isentropic process, which is:
v = sqrt(2 * Cp * (T1 - T2))
Where v is the velocity of the gas, Cp is the specific heat at constant pressure for air at room temperature, T1 is the temperature at the turbine inlet, and T2 is the temperature at the turbine exit.
v = sqrt(2 * 1005J/kgK * (1400K - 882.6K)) = 598.6m/s
Therefore, the velocity of the exhaust gases is 598.6m/s.
(d) The propulsive power developed in kW can be determined using the equation for the power of a jet engine, which is:
P = m * (v2 - v1)
Where P is the power, m is the mass flow rate of air, v2 is the velocity of the exhaust gases, and v1 is the velocity of the turbojet.
P = 40Kg/s * (598.6m/s - 320m/s) = 11144kW
Therefore, the propulsive power developed is 11144kW.
(e) The propulsive efficiency can be determined using the equation for the efficiency of a jet engine, which is:
eta = (P / Q) * 100%
Where eta is the efficiency, P is the power, and Q is the heat input.
Given the power of 11144kW and the heat input of 42,700 kJ/kg * 40Kg/s = 1708000kW, we can calculate the propulsive efficiency as follows:
eta = (11144kW / 1708000kW) * 100% = 0.65%
Therefore, the propulsive efficiency is 0.65%.
(f) The rate of fuel consumption in kg/s can be determined using the equation for the heat input, which is:
Q = m * HV
m = 1708000kW / (42,700 kJ/kg * 1 kW / 1000 kJ) = 40Kg/s
Therefore, the rate of fuel consumption is 40Kg/s.
Learn more about the Brayton cycle here: https://brainly.com/question/29611107
#SPJ11
as in assignment 8, a complete binary tree of threads should be created. each leaf thread will compute the hash value of n/m consecutive blocks assigned to it and return the hash value to its parent thread (through pthread exit() call). an interior thread will compute the hash value of the blocks assigned to it, and then wait for its children to return hash values. these hash values should be combined to form a string: . (note that the sign here means concatenation and not addition. also, if the interior thread has no right child, only the hash value of the interior thread and the hash value from the left child are combined.) the interior thread then computes hash value of the concatenated string as before and returns the value to its parent, the value returned by the root thread is the hash value of the file. how to assign blocks to threads? each thread is assigned a number when it is created. the number of root thread is 0. for a thread with number i, the number of its left child is 2 * i 1, and the number of its right child is 2 * i 2. for a thread with number i, n/m consecutive blocks starting from block number i * n/m are assigned. for example, let n
Answers
This is the code for a complete binary tree of threads should be created. each leaf thread will compute the hash value of n/m consecutive blocks assigned to it and return the hash value to its parent thread (through pthread exit() call).
Step-by-step coding:
#include <stdio.h>
#include <stdlib.h>
#include <stdint.h>
#include <inttypes.h>
#include <errno.h> // for EINTR
#include <fcntl.h>
#include <unistd.h>
#include <sys/types.h>
#include <sys/stat.h>
// Print out the usage of the program and exit.
void Usage(char*);
uint32_t hashBlk(int);
uint32_t jenkins_one_at_a_time_hash(const uint8_t* , size_t );
#define BSIZE 4096
uint32_t* htable;
int
main(int argc, char** argv)
{
int32_t fd;
uint32_t nblocks;
char carray[BSIZE];
// input checking
if (argc != 3)
Usage(argv[0]);
// open input file
fd = open(argv[1], O_RDWR);
if (fd == -1) {
perror("open failed");
exit(EXIT_FAILURE);
}
// use fstat to get file size
// calculate nblocks
printf(" no. of blocks = %u \n", nblocks);
double start = GetTime();
// calculate hash of the input file
double end = GetTime();
printf("hash value = %u \n", hash);
printf("time taken = %f \n", (end - start));
close(fd);
return EXIT_SUCCESS;
}
uint32_t
jenkins_one_at_a_time_hash(const uint8_t* key, size_t length) {
size_t i = 0;
uint32_t hash = 0;
while (i != length) {
hash += key[i++];
hash += hash << 10;
hash ^= hash >> 6;
}
hash += hash << 3;
hash ^= hash >> 11;
hash += hash << 15;
return hash;
}
void
Usage(char* s) {
fprintf(stderr, "Usage: %s filename height \n", s);
exit(EXIT_FAILURE);
}
To learn more about binary tree, visit: https://brainly.com/question/16644287
#SPJ4
Which of these items can be used as an electronic studying schedule
Answers
Type the correct answer in the box. Spell all words correctly.
What does Clara create that programmers can use to write code?
Clara works in a software development company. Her boss identifies that she has strong problem-solving skills. Clara’s boss places her on the planning team to create____ for programmers.
This is for Edmentum final! thanks
Answers
Answer:
design documents
Explanation:
Usually, in a software development company or information technology (IT) department, software is developed through a team effort. Such teams have programmers and various other professionals, such as software developers and engineers. These professionals perform parts of the entire software development process. For example, the programmer is not the only person in a team who can formulate a solution to a problem. Many times, software developers and system analysts do this. They create design documents for the programmer to follow. Based on these design documents, a programmer writes the code for the program.
An algorithm is a guiding rule used to solve problems or make decisions. Please select the best answer from the choices provided T F
Answers
True. An algorithm can be defined as a step-by-step procedure or a set of rules designed to solve a specific problem or perform a particular task.
It serves as a guiding rule for problem-solving or decision-making processes. Algorithms are used in various fields, including computer science, mathematics, and even everyday life.
In computer science, algorithms are fundamental to programming and software development. They provide a systematic approach to solving complex problems by breaking them down into smaller, manageable steps.
Algorithms can range from simple and straightforward to highly complex, depending on the nature of the problem they aim to solve.
The importance of algorithms lies in their ability to provide a structured and efficient solution to a given problem. They help in achieving consistency, accuracy, and reproducibility in decision-making processes. Additionally, algorithms enable automation and optimization, allowing for faster and more reliable problem-solving.
It is essential to acknowledge and respect the originality and intellectual property of others when using algorithms developed by someone else. Proper citation and avoiding plagiarism are crucial to ensure the integrity of one's work and uphold ethical standards.
For more such questions on algorithm,click on
https://brainly.com/question/29927475
#SPJ8
User inserts 10 numbers. Write a program that will show if there are more positive or negative numbers among the entered numbers.
Answers
Here is a basic program that I wrote. This will check how many positive/negative numbers are in the table and then prints the amount..
Using Python
# list of numbers
list1 = [10, -21, 4, -45, 66, -93, 1]
pos_count, neg_count = 0, 0
# iterating each number in list
for num in list1:
# checking condition
if num >= 0:
pos_count += 1
else:
neg_count += 1
print("Positive numbers: ", pos_count)
print("Negative numbers: ", neg_count)
When an entrepreneur has three employees at a busy and growing software company, what is the primary responsibility of the employees?
create the product that customers want
explain business decisions to stakeholders
identify and contact financial investors
select new types of software to sell
Answers
Answer:
A: Create the product that customers
Explanation:
I did it on edgy
Answer:
(A). Create the product that customers want
Explanation:
I got it right on edge2020.
There are two main types of hard drive available to a computer. State what they are and describe their use.
(best answer gets to be the brainliest!)
Answers
Answer:
Hard disk drives (HDD), which use one or more rotating discs and rely on magnetic storage, and solid-state drives (SSD), which have no moving mechanical parts, but use flash memory like the kind found in USB flash drives.
Explanation:
Which occupation is in the Manufacturing career cluster? A)tax auditor B)website developer C)truck driver D)machinist
Answers
Answer:
Macinist
Explanation:
It would be a machanist because a tax auditor and website devolper would be some sort of career clust that would include something about technology.
Then a truck drivier is transportation. The last one left is machinist and that is a person that uses machines to make/ build things, so that is the one that makes the most sense.
The occupation that is in the Manufacturing career cluster is a machinist. The correct option is D).
What is the Manufacturing career cluster?A manufacturing cluster is a network of connected companies with similar goals situated in a single geographic area. They profit from collaborative growth and share common industry traits.
It would be a mechanic, as a tax auditor and website developer are two professions that include some aspect of technology. Direct materials, direct labor, and overhead are the three main types of expenditures that are incurred during the manufacturing process.
Then transportation is a truck driver. The one that makes the most sense is the last one, "machinist," which is defined as a person who utilizes machines to create or construct things.
Therefore, the correct option is D) machinist.
To learn more about the career cluster, visit here:
https://brainly.com/question/15225914
#SPJ2
Which specialized computer component would be most important for a workstation built for audio and video editing?.
Answers
The specialized computer component would be most important for a workstation built for audio and video editing is option C: a specialized video card.
What do special purpose cards in computers do?
A system can be expanded with specialized cards. There are graphics cards, network cards, and TV tuner cards. A component that handles the screen's graphics is called a graphics card. Its responsibility is to produce each image and piece of text on the screen. It uses pixels, which are teeny, tiny dots, to create the text and images.
Note that Specialized inputs and outputs are required for recording and playback devices on computers made for audio and video editing. A video and audio card with the necessary input and output flexibility is required for this.
Learn more about video card from
https://brainly.com/question/26281658
#SPJ1
See full question below
Which specialized computer component would be most important for a workstation built for audio and video editing?
a TV tuner card
a high speed wireless adapter
a specialized video card
a liquid CPU cooling system
In an "and" operator only ONE value has to be true to activate the if block
Yes or No
(Scratch Coding)
Answers
If the "and" operator is present, BOTH conditions must be True in order for the if block to be activated.
Answer:
No
Explanation:
Data ________ is important because it establishes an organization's rules for sharing, disseminating, acquiring, standardizing, and classifying data.
Answers
Data protection policy is important because it establishes an organization's rules for acquiring, standardizing and disseminating data.
What is Data protection policy?These are policies adopted by organizations that help to ensure data is adequately protected.
When data isn't protected , it could get to the hands of criminals which could use it for different types of cybercrime and also to ensure compliance with data protection laws in the country.
Read more about Data protection policy here https://brainly.com/question/26493645
Create a paper of at least 1,800 words describing the situation you selected and explaining the logic that would support an array.
Answers
Answer:
I dont know about 1800 words but I sure can tell you abit about array
Explanation: Array in simple sense refers to a collection of similar data. It holds data which is homogeneous in nature, meaning they are all alike. The use of array provide a lot of advantages in the fields of computer programming. When you declare a variable for an array, you can store as much data as you wish in the same variable without having to declare many variables. A 2X2 dimensional array can also be used in programming which represents matrices as well. The search process in an array too is really convenient and time saving. Also in an array, accessing an element is very easy by using the index number.
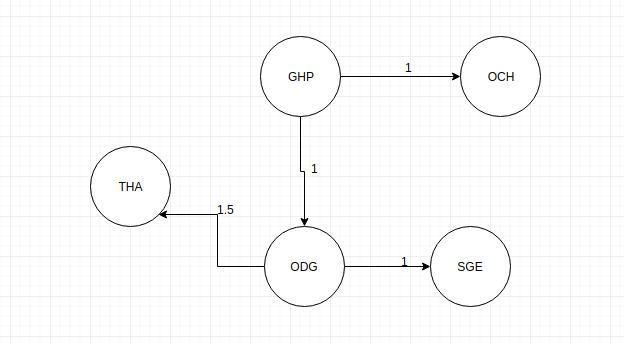
use prim's algorithm to find a minimal spanning tree for the times whose vertices are the hotels given in the distance chart. what is the total time for this spanning tree?
Answers
The greedy approach is the foundation of the Prim's algorithm. We choose the edge with the least weight at each step, assuming that the final node hasn't been reached yet.
The spanning tree would appear like this. All the names are written in shorthand. Kindly corelate.
What is spanning tree?
A spanning tree is a sub-graph of an undirected connected graph that contains all of the graph's vertices and the fewest number of edges possible between them. It is not a spanning tree if a vertex is missed. Weights may or may not be applied to the edges.
What is minimum spanning tree?
A minimum spanning tree is one in which the weight of the edges added together is as small as it can be.
To know more about spanning tree, check out:
https://brainly.com/question/13148966
#SPJ1
please can someone help my assignment.
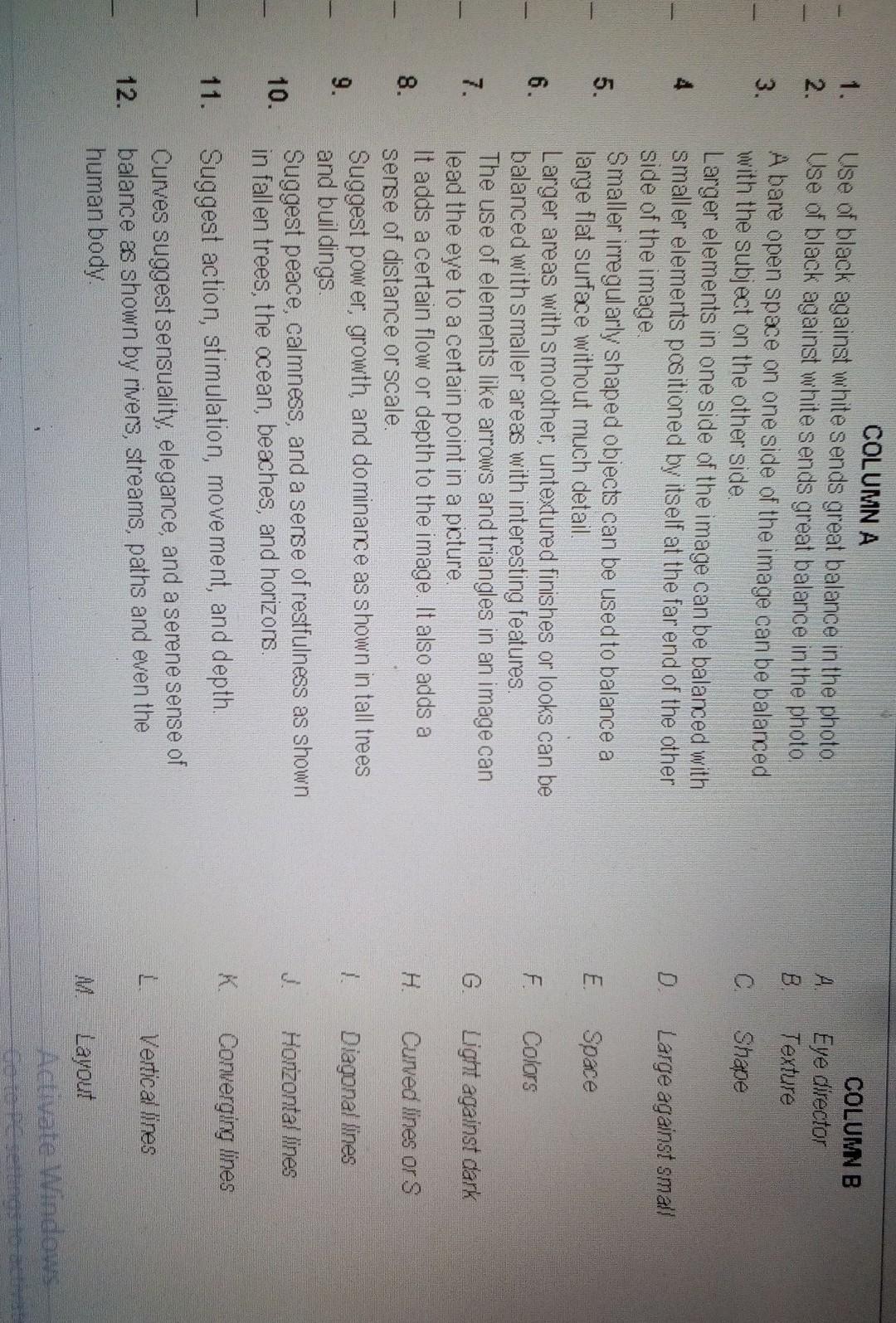
Answers
Light against dark- Smaller irregularly shaped objects can be used to balance a large flat surface without much detail.
Curved lines or smooth textures Larger areas with smoother, untextured finishes or looks can be balanced with smaller areas with interesting features.
Horizontal lines - The use of elements like arrows and triangles in an image can lead the eye to a certain point in a picture.
Converging lines adds a certain flow or depth to the image. It also adds a sense of distance or scale.
Vertical lines Suggest power, growth, and dominance as shown in tall trees and buildings.
Large against small is when Larger elements in one side of the image can be balanced with smaller elements positioned by itself at the far end of the other side of the image.
Diagonal lines suggest peace, calmness, and a sense of restfulness as shown by rivers, streams, paths, and even the human body.
Symmetrical balance is achieved when the two halves of an image are mirror images of each other.
Asymmetrical balance is achieved when the two halves of an image are not mirror images of each other, but they still feel balanced.
Radial balance is achieved when the elements in an image are arranged around a central point.
How to explain the informationCurved lines are often seen as being more organic and natural, while straight lines are seen as being more geometric and artificial. Smooth textures can also create a sense of calm and serenity, while rough textures can create a sense of energy and excitement.
Horizontal lines can create a sense of stability and balance, while vertical lines can create a sense of height and power. Arrows and triangles are directional elements that can be used to lead the eye to a certain point in an image. They can also be used to create a sense of movement or energy.
Learn more about elements on
https://brainly.com/question/20096027
#SPJ1
Hello, please explain how to solve this problem.A last-mile delivery service is looking into increasing capacity by purchasing new delivery vans. Two vans are being considered. Van A costs $50,000 with a variable cost of $12.00 per average delivery, all inclusive of gasoline, insurance, etc. Van B costs $70,000 with a variable cost of $11.00 per average delivery. The company is also considering a courier service which requires a $60,000 non-refundable joiner fee and a variable cost of $13.00 per average delivery. Last but not least the company is also considering a new drone delivery option that requires an investment in infrastructure of $100,000 and a delivery cost of $15.00 per delivery, but costs are expected to drop sharply in the foreseeable future.a. _____ is preferred at volumes below _____, while _____ is preferred at volumes above _____.b. If the average sales revenue generated by the delivery service $15.00 per delivery, but customers are willing to pay $20.00 for the novelty of drone delivery, what is the breakeven in units for each option?
Answers
a. We must compute the total cost for each alternative at various levels of delivery in order to evaluate which is favoured at certain volume levels. Assume for the moment that we are contrasting the two vans, the courier, and the drone delivery alternative.
Total cost is the term used to describe the total cost of manufacturing, which includes both fixed and variable costs. The cost necessary to manufacture a good is referred to as the whole cost in economics. The upfront cost of a purchase is simple to determine; the difficult part is predicting the hidden expenditures. Understanding indirect costs that accumulate over the course of a product's lifecycle, such as maintenance, support, and licence fees, is made easier with the use of a TCO study. A crucial idea in economics is the concept of cost. It speaks of the sum paid in order to obtain any goods or services.
Learn more about total cost here:
https://brainly.com/question/14545701
#SPJ4
how do i turn off itallics on a school chromebook i accidentally turned them on in another tab and i dont know how to undo them
Answers
Drag the tiles to the correct boxes to complete the pairs.
Match the testing tools to their use.
Selenium
JMeter
load testing tool
functional testing tool
test management tool
defect-tracking tool
QTP
web browser automation tool
Quality Center
Bugzilla
Answers
Answer:
JMeter is a functional testing tool
Can you see who tries to access a password-protected file, but does not put in the password?
Answers
Yes/no
Explanation:
Depending on the person.
Yes, if your cousins,parents,etc have opened it.
No, if people like hackers have done it.
What are 3 similarities and 3 differences between live theatre and film/videos -Drama Class
Answers
1. Theatre is live. Film has been captured in the past. We only see after the making process is done.
2.You have chance for improvement in each theatre shows but its impossible in Films. Once film is done its done.
3.Normally Theatre is cheaper, films are costly.
Similarities-
1.Theatre and films both are arts, so many varieties of arts melt into theatre or film to make it happen.
2.Theatre and films both are very effective medium of communication.
3.Theatre and films both are considered as great form of Entertainment.
in order to move from the /home/joe/test/data to the /home/joe directory, what command should be issued?
Answers
If the current working directory needs to be displayed, cd../..command should be used.
Which command should be used to remove every file from the root directory of a drive or directory?Complete Response. Hierarchical storage is used for directories. The addresses in the memory are kept in a tree structure by this hierarchy, and if the user wants to erase those addresses, they must first delete the entire tree by executing the command Deltree.
Which of the following keys would compel a user to enter command mode back in the vi editor?You can insert text, move to a new line with the Enter key, traverse the text with the arrow keys, and use vi as a free-form text editor when in Insert mode.
To know more about command visit:-
https://brainly.com/question/29978995
#SPJ4
Which statement of the visualization is incorrect? A) Virtualization works on the desktop, allowing only one operating system(Mac OS, Linux, or Windows) to run on the platform B) A server running virtualization software can create smaller compartments in memory that each behaves like a separate computer with its own operating system and resources C) Virtualization is referred to as the operating system for operating systems D) Virtualization can generate huge savings for firms by increasing the usage of their hardware capacity.
Answers
The incorrect statement is A) Virtualization works on the desktop, allowing only one operating system (Mac OS, Linux, or Windows) to run on the platform. Virtualization on the desktop enables the concurrent execution of multiple operating systems.
Explanation:
A) Virtualization works on the desktop, allowing only one operating system (Mac OS, Linux, or Windows) to run on the platform.
This statement is incorrect because virtualization on the desktop allows multiple operating systems to run concurrently on the same platform. Virtualization software, such as VMware or VirtualBox, enables users to create and run virtual machines (VMs) that can host different operating systems simultaneously, including Mac OS, Linux, and Windows.
B) A server running virtualization software can create smaller compartments in memory that each behaves like a separate computer with its own operating system and resources.
This statement is correct. Virtualization software allows the creation of virtual compartments or containers within a server's memory. Each compartment, known as a virtual machine, can operate independently with its own dedicated operating system and allocated resources.
C) Virtualization is referred to as the operating system for operating systems.
This statement is correct. Virtualization is often referred to as the "operating system for operating systems" because it provides a layer of abstraction and management for multiple operating systems running on the same physical hardware.
D) Virtualization can generate huge savings for firms by increasing the usage of their hardware capacity.
This statement is correct. Virtualization enables efficient utilization of hardware resources by consolidating multiple virtual machines onto a single physical server. This consolidation reduces the need for additional physical servers, leading to cost savings in terms of hardware procurement, maintenance, and power consumption.
To know more about operating system visit :
https://brainly.com/question/29532405
#SPJ11
Which of the following is the correct UNC path to use when mapping a network drive?
A. \sharepassword
B. \shareserver
C. \serverusername
D. \servershare
Answers
The correct UNC path to use when mapping a network drive is D. \servershare.
UNC stands for "Universal Naming Convention," which is a standard way of referring to network resources in Windows. The UNC path for a shared network folder consists of the name of the server that is hosting the share and the name of the share itself, separated by a backslash () character. In the UNC path \servershare, "server" represents the name of the computer or server that is hosting the share, and "share" represents the name of the shared folder or resource. This path would be used to map a network drive to the shared folder on the server. Option A, \sharepassword, does not include the server or share names and is therefore not a valid UNC path. Option B, \shareserver, is also incorrect because the server and share names are reversed. Option C, \serverusername, would be used to access a user's home folder on the server, but is not a valid UNC path for mapping a network drive to a shared folder.
Learn more about network here:
https://brainly.com/question/14601830
#SPJ11
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
Explain the following term ( a) GUI ( b) WIMP
please give me the answer of this question
don't spam
Answers
Explanation:
here you go mark my brainlist plzz

Consider the IP address 10.2.3.147 with network mask 255.255.255.240.
What is the subnet number?
What is the directed broadcast of the network?
Answers
subnet number of the given IP address with network mask 255.255.255.240 is 10.2.3.144, and the directed broadcast of the network is 10.2.3.159.
To find the subnet number and directed broadcast of the given IP address and network mask, we first need to convert both into binary form.
IP Address: 10.2.3.147
Binary: 00001010.00000010.00000011.10010011
Network Mask: 255.255.255.240
Binary: 11111111.11111111.11111111.11110000
To find the subnet number, we need to perform a bitwise AND operation between the IP address and network mask.
IP Address: 00001010.00000010.00000011.10010011
Network Mask: 11111111.11111111.11111111.11110000
Result: 00001010.00000010.00000011.10010000
The subnet number is the network portion of the result, which in this case is 10.2.3.144.
To find the directed broadcast of the network, we need to perform a bitwise OR operation between the IP address and the bitwise complement of the network mask.
IP Address: 00001010.00000010.00000011.10010011
Network Mask: 11111111.11111111.11111111.11110000
Bitwise Complement of Mask: 00000000.00000000.00000000.00001111
Result: 00001010.00000010.00000011.11111111
The directed broadcast of the network is the broadcast address of the subnet, which in this case is 10.2.3.159.
To know more about address visit:
brainly.com/question/31960726
#SPJ11