A contiguous subsequence of a list S is a subsequence made up of consecutive elements of S. For example, if S is 5,15,-30,10,-5,40,10 then 5,15,-30 is a contiguous subsequence but 5,15,40 is not.
1. Give a linear-time algorithm for the following task:
Input: A list of numbers, A(1), . . . , A(n).
Output: The contiguous subsequence of maximum sum (a subsequence of length zero has sum zero).
For the preceding example, the answer would be 10,-5,40,10 with a sum of 55.
Answers
Answer:
We made use of the dynamic programming method to solve a linear-time algorithm which is given below in the explanation section.
Explanation:
Solution
(1) By making use of the dynamic programming, we can solve the problem in linear time.
Now,
We consider a linear number of sub-problems, each of which can be solved using previously solved sub-problems in constant time, this giving a running time of O(n)
Let G[t] represent the sum of a maximum sum contiguous sub-sequence ending exactly at index t
Thus, given that:
G[t+1] = max{G[t] + A[t+1] ,A[t+1] } (for all 1<=t<= n-1)
Then,
G[0] = A[0].
Using the above recurrence relation, we can compute the sum of the optimal sub sequence for array A, which would just be the maximum over G[i] for 0 <= i<= n-1.
However, we are required to output the starting and ending indices of an optimal sub-sequence, we would use another array V where V[i] would store the starting index for a maximum sum contiguous sub sequence ending at index i.
Now the algorithm would be:
Create arrays G and V each of size n.
G[0] = A[0];
V[0] = 0;
max = G[0];
max_start = 0, max_end = 0;
For i going from 1 to n-1:
// We know that G[i] = max { G[i-1] + A[i], A[i] .
If ( G[i-1] > 0)
G[i] = G[i-1] + A[i];
V[i] = V[i-1];
Else
G[i] = A[i];
V[i] = i;
If ( G[i] > max)
max_start = V[i];
max_end = i;
max = G[i];
EndFor.
Output max_start and max_end.
The above algorithm takes O(n) time .
Related Questions
Most operating system have GUI as part of the system, which is the following best describes an operating system GUI
Answers
A Graphical User Interface (GUI) is the component of an operating system that allows users to communicate with the system using graphical elements. GUIs are generally used to give end-users an efficient and intuitive way to interact with a computer.
They provide an easy-to-use interface that allows users to manipulate various objects on the screen with the use of a mouse, keyboard, or other input device.The primary function of an operating system GUI is to make it easier for users to interact with the system.
This is done by providing visual feedback and a simple way to access various system functions. GUIs can be customized to suit the user's preferences, which means that they can be tailored to meet the specific needs of different users.Some of the key features of a GUI include the use of windows, icons, menus, and buttons.
Windows are used to display information and applications, while icons are used to represent various objects or applications on the screen. Menus and buttons are used to provide users with a way to access various system functions, such as saving a file or printing a document.
The use of a GUI has become a standard feature of most operating systems. This is because GUIs make it easier for users to interact with computers, and they provide an efficient and intuitive way to access various system functions.
For more such questions on Graphical User Interface, click on:
https://brainly.com/question/28901718
#SPJ8
You were just hired as an IT Specialist for Smalltown School District. Your first assignment is to review a problem area& in student records processing. It seems that the program currently used to compute student grade point averages and class rankings runs terribly slow and as a result end of year reports are habitually late. Your are asked to come up with a list of items that should be checked in order to determine if a modification to code is in order. The IT department head is asking you to do this without the opportunity to actually see the current application/programs in use. What questions would you ask about the current code? What areas of code would you look at? What would you need to know about the student data?
Answers
Answer:
Explanation:
There are various questions that you can ask in this scenario, such as
What grading policies are being implemented?
How many student grades are being calculated by the program?
What is the requirements for a student to pass?
All of these questions would allow you to get an idea of how extensive the code may be and its complexity. Once you know this you would look at the code revolving around actually looping through the data and doing the necessary calculations. You can then determine how to manipulate the code and make it much more efficient.
You would also need to know how the student data is being saved, which will help determine if it is the best data structure for saving this type of data or if it can be replaced in order to maintain the data secure while increasing the speed of the program. Mainly since this information needs to be continuously used from the data structure.
give one major environmental and
one energy problem kenya faces as far as computer installations are concerned?
Answers
One considerable predicament that Kenya encounters pertaining to the utilization of computers is managing electronic waste (e-waste).
Why is this a problem?The mounting number of electronic devices and machines emphasizes upon responsibly discarding outdated or defective hardware in order to avoid environmental degradation.
E-waste harbors hazardous materials such as lead, mercury, and cadmium which can pollute soil and water resources, thereby risking human health and ecosystem sustainability.
Consequently, a significant energy drawback with computer use within Kenya pertains to the insufficiency or instability of electrical power supply.
Read more about computer installations here:
https://brainly.com/question/11430725
#SPJ1
Which of the following is a positional argument?
a) ABOVE
b) MIN
c) AVERAGE
d) MAX
Answers
You are the IT administrator for a small corporate network. You have just changed the SATA hard disk in the workstation in the Executive Office. Now you need to edit the boot order to make it consistent with office standards. In this lab, your task is to configure the system to boot using devices in the following order: Internal HDD. CD/DVD/CD-RW drive. Onboard NIC. USB storage device. Disable booting from the diskette drive.
Answers
Answer:
this exercise doesn't make sense since I'm in IT
Explanation:
Why is the insertion sort algorithm useful when you need to conserve memory?
A. because it is fast
B. because it is performed in place
C. because it is efficient
D. because it creates a temporary array and destroys it quickly
Answers
Answer:
B. because it is performed in place
Explanation:
For the PLATO test
feature of word processing
Answers
Answer:
the word processing
Explanation:
the word is a good word
Declare a Boolean variable named isValidPasswd. Use isValidPasswd to output "Valid" if codeStr contains no more than 4 letters and codeStr's length is less than 9, and "Invalid" otherwise.
Ex: If the input is l7J45s6f, then the output is:
Valid
Ex: If the input is n84xfj061, then the output is:
Invalid
Note: isalpha() returns true if a character is alphabetic, and false otherwise. Ex: isalpha('a') returns true. isalpha('8') returns false.
please help in c++
Answers
Answer: #include <iostream>
#include <string>
using namespace std;
int main() {
string codeStr = "l7J45s6f";
bool isValidPasswd = true;
int letterCount = 0;
for (char c : codeStr) {
if (isalpha(c)) {
letterCount++;
}
if (letterCount > 4 || codeStr.length() >= 9) {
isValidPasswd = false;
break;
}
}
if (isValidPasswd) {
cout << "Valid" << endl;
} else {
cout << "Invalid" << endl;
}
return 0;
}
Explanation: In this usage, we to begin with characterize a codeStr variable with the input string, and a isValidPasswd variable initialized to genuine. We at that point circle through each character in codeStr, increasing a letterCount variable in case the current character is alphabetic. In case the letterCount gets to be more noteworthy than 4, or in the event that the length of codeStr is more prominent than or break even with to 9, we set isValidPasswd to wrong and break out of the circle.
At last, we yield "Substantial" in case isValidPasswd is genuine, and "Invalid" something else.
Answer:
c++
Explanation:
write a script that(1) gets from a user: (i) a paragraph of plain text and (ii) a distance value.distance value. next, (2) encrypt the plaintext using caesar cipher and (3) output (print) this paragraph into an encrypted text. (4) write this text to file called ‘encryptfile.txt’ and print the text file. Then (5) read this file and write it to a file named ‘copyfile.txt’ and print text file.
Answers
A script that(1) gets from a user: (i) a paragraph of plain text and (ii) a distance value.distance value. next, encrypts the text using Caeser cipher, then prints it as an encrypted text given below:
The below script also reads the file and then writes it to a file named ‘copyfile.txt’ and print the text file.
The Scriptmapping = {}
with open ( " copyfile . txt " , " r " ) as keyFile:
for line in copyFile:
l1, l2 = line . split ( )
mapping [ upper ( l1 ) ] = upper ( l2 )
decrypt = " "
with open ( " encrypted.txt " , " r " ) as encryptedFile:
for line in encryptedFile:
for char in line:
char = upper ( char )
if char in mapping:
decrypt + = mapping [ char ]
else:
decrypt += char print ( decrypt )
Read more about programming here:
https://brainly.com/question/16397886
#SPJ1
How dose society use computer in finance?
Answers
☁️ Answer ☁️
annyeonghaseyo!
Your answer is:
"Computers are able to calculate things faster than any human can, and they're a lot cheaper to maintain than it is to pay a human. Computers don't make mistakes so people rely on them to make massive calculations 100% accurately."
Hope it helps.
Have a nice day hyung/noona!~  ̄▽ ̄❤️
List 5 properties and metrics for specifying non-functional requirements.
Answers
Answer:
- performance
scalability
capacity
availability
reliability
The issue “when a user deletes the data, whether all the copies are deleted or not is something that every needs to have a clear answer to” comes under which of the following?
Answers
The issue “when a user deletes the data, whether all the copies are deleted or not is something that every needs to have a clear answer to” comes under aspect of data deletion and data lifecycle management.
What is the deletion?One need rules and practices to delete data to follow privacy laws, protect data, and meet user expectations. When a user gets rid of data, it is important to check if all copies of that data have been effectively removed from the system or storage.
Data Retention Policies: Organizations must create clear rules about how long they will keep certain data before getting rid of it.
Read more about deletion here:
https://brainly.com/question/30280833
#SPJ1
Analyze the needs of the National Security team and help them articulate its problems, develop solutions to meet its needs, and deliver a recommendation that is aligned with the extant national objectives.
Answers
Answer:
Following are the solution to this question:
Explanation:
The Council's role has been to assist and support the President regarding national security and foreign policies ever since its inception under Truman. This Committee often acts as the primary arm of a President to organize these initiatives between government agencies.
The Leader holds sway over the NSC. Its Secretary Of Defense offers a range of options for the Administration on policy issues. The director of national intelligence helps prepare the administration's foreign travel, among other tasks, and offers context memos and staffing for the administration's discussions and phone interviews involving global leaders.
Safety investments were taken for many years utilizing threat cost-benefit analysis wherein the effect metric has been largely focused on even a risk reduction comparative estimate. To evaluate investment decisions, most aim to conduct similar analyses.
Even so, the potential threat is much harder to measure for high-security installations that potential hazard since the likelihood of an attack is highly uncertain and depends strongly on undefinable psychological factors like deterrence as well as the intensity of enemy goals.
What is the main reason for assigning roles to members of a group?
Answers
So that people with strengths in different areas can work on what they do best, plus it divides the workload.
Write a program that reads a file name from the keyboard. The file contains integers, each on a separate line. The first line of the input file will contain the number of integers in the file. You then create a corresponding array and fill the array with integers from the remaining lines. If the input file does not exist, give an appropriate error message and terminate the program. After integers are stored in an array, your program should call the following methods in order, output the intermediate results and count statistics on screen, and at end output even integers and odd integers to two different files called even.out and odd.out.
Implement the following methods in the program:
* public static int[] inputData() – This method will ask user for a file name, create an array, and store the integers read from the file into the array. If input file does not exist, give an appropriate error message and terminate the program.
* public static void printArray(int[] array) – This method will display the content of the array on screen. Print 10 integers per line and use printf method to align columns of numbers.
public static void reverseArray(int[] array) – This method will reverse the elements of the array so that the 1st element becomes the last, the 2nd element becomes the 2nd to the last, and so on.
* public static int sum(int[] array) – This method should compute and return the sum of all elements in the array.
* public static double average(int[] array) – This method should compute and return the average of all elements in the array.
* public static int max(int[] array) – This method should find and return the largest value in the array.
* public static int min(int[] array) – This method should find and return the smallest value in the array.
* public static void ascendingSelectionSortArray(int[] array) – This method will use Selection Sort to sort (in ascending order) the elements of the array so that the 1st element becomes the smallest, the 2nd element becomes the 2nd smallest, and so on.
* public static void desendingBubbleSortArray(int[] array) – This method will Bubble Sort to sort (in descending order) the elements of the array so that the 1st element becomes the largest, the 2nd element becomes the 2nd largest, and so on.
* public static void outputData(int[] array) – This method will create two output files called even.out and odd.out. Scan through the entire array, if an element is even, print it to even.out. If it is odd, print the element to odd.out.
Answers
Answer:
Explanation:
import java.util.Scanner;
import java.io.*;
public class ArrayProcessing
{
public static void main(String[] args) throws IOException
{
Scanner kb = new Scanner(System.in);
String fileName;
System.out.print("Enter input filename: ");
fileName = kb.nextLine();
File file = new File(fileName);
if(!file.exists())
{
System.out.println("There is no input file called : " + fileName);
return;
}
int[] numbers = inputData(file);
printArray(numbers);
}
public static int[] inputData(File file) throws IOException
{
Scanner inputFile = new Scanner(file);
int index = 1;
int size = inputFile.nextInt();
int[] values = new int[size];
while(inputFile.hasNextInt() && index < values.length)
{
values[index] = inputFile.nextInt();
index++;
}
inputFile.close();
return values;
}
public static void printArray(int[] array)
{
int count = 1;
for (int ndx = 1; ndx < array.length; ndx++)
{
System.out.printf("%5.f\n", array[ndx]);
count++;
}
if(count == 10)
System.out.println("");
}
}
Describe what test presentation and conclusion are necessary for specific tests in IT testing such as
-resource availability
-environment legislation and regulations (e.g. disposal of materials)
- work sign off and reporting
Answers
For specific tests in IT testing, the following elements are necessary.
What are the elements?1. Test Presentation - This involves presenting the resources required for the test, ensuring their availability and readiness.
2. Conclusion - After conducting the test, a conclusion is drawn based on the results obtained and whether the objectives of the test were met.
3. Resource Availability - This test focuses on assessing the availability and adequacy of resources required for the IT system or project.
4. Environment Legislation and Regulations - This test evaluates compliance with legal and regulatory requirements related to environmental concerns, such as proper disposal of materials.
5. Work Sign Off and Reporting - This includes obtaining formal approval or sign off on the completed work and preparing reports documenting the test outcomes and findings.
Learn more about IT testing at:
https://brainly.com/question/13262403
#SPJ1
what's the difference between natural systems and man made systems
Answers
Answer:
Natural systems are already in place while man made systems were created by humans manipulating things in some way.
Explanation:
man made: human created
natural systems: existed without interference
Select the true statement below. A. Using tables can improve your search engine optimization. B. Content contained within Flash media is invisible to search engines. C. Your HTML code must be valid in order to be listed in search engine results. D. Descriptive page titles and heading tags with appropriate keywords can help with search engine optimization.
Answers
Answer:
D. Descriptive page titles and heading tags with appropriate keywords can help with search engine optimization.
Explanation:
Search engine optimization (SEO) can be defined as a strategic process which typically involves improving and maximizing the quantity and quality of the number of visitors (website traffics) to a particular website by making it appear topmost among the list of results from a search engine such as Goo-gle, Bing, Yah-oo etc.
This ultimately implies that, search engine optimization (SEO) helps individuals and business firms to maximize the amount of traffic generated by their website i.e strategically placing their website at the top of the results returned by a search engine through the use of algorithms, keywords and phrases, hierarchy, website updates etc.
Hence, search engine optimization (SEO) is focused on improving the ranking in user searches by simply increasing the probability (chances) of a specific website emerging at the top of a web search.
Typically, this is achieved through the proper use of descriptive page titles and heading tags with appropriate keywords. Also, the first step in adding a website to a search engine service is to index your webpages by adding appropriate keywords and description meta tags.
Consider the following argument: Any piece of software that is in the public domain may be copied without permission or fee. But that cannot be done in the case of software under copyright. So, software under copyright must not be in the public domain. The conclusion of the argument is:
Answers
Answer:
"software under copyright must not be in the public domain"
Explanation:
The conclusion of his argument is "software under copyright must not be in the public domain". This combines the two premises that were stated before it in order to form a logical outcome based on the premises. In the case of logic, this would basically be an
IF A and IF B, Then C
type of logic, in which A is "Public Domain Work can be copied", B is "Software under Copyright cannot be copied", and C is the conclusion which would be "software under copyright must not be in the public domain"
You are developing an application to ingest and process large volumes of events and data by using Azure Event Hubs.
You must use Azure Active Directory (Azure AD) to authorize requests to Azure Event Hubs resources.
Answers
Note that it is TRUE to state that you must use Azure Active Directory (Azure AD) to authorize requests to Azure Event Hubs resources.
How is this so?Azure Event Hubs, a data streaming platform,can be integrated with Azure Active Directory (Azure AD) for authentication and authorization purposes.
This ensures that requests to access and utilize Event Hubs resources are authorized and controlled through Azure AD, providing secure and authorized access to the application.
Learn more about Azure Active Directory at:
https://brainly.com/question/28400230
#SPJ1
You are developing an application to ingest and process large volumes of events and data by using Azure Event Hubs.
You must use Azure Active Directory (Azure AD) to authorize requests to Azure Event Hubs resources.
True or False?
Write a program whose input is a string which contains a character and a phrase, and whose output indicates the number of times the character appears in the phrase.
Ex: If the input is:
n Monday
the output is:
1
Ex: If the input is:
z Today is Monday
the output is:
0
Ex: If the input is:
n It's a sunny day
the output is:
2
Case matters.
Ex: If the input is:
n Nobody
the output is:
0
n is different than N.
Learning Python
Answers
Explanation:
1
Ex: If the input is:
z Today is Monday
the output is:
0
Ex: If the input is:
n It's a sunny day
the output is:
2
Case matters.
Ex: If the input is:
n Nobody
the output is:
0
n is different than N.
Learning Python
I've included my code in the picture below. Best of luck.
a. Draw the hierarchy chart and then plan the logic for a program needed by Hometown Bank. The program determines a monthly checking account fee. Input includes an account balance and the number of times the account was overdrawn. The output is the fee, which is 1 percent of the balance minus 5 dollars for each time the account was overdrawn. Use three modules. The main program declares global variables and calls housekeeping, detail, and end-of-job modules. The housekeeping module prompts for and accepts a balances. The detail module prompts for and accepts the number of overdrafts, computes the fee, and displays the result. The end-of-job module displays the message Thanks for using this program.
b. Revise the banking program so that it runs continuously for any number of accounts. The detail loop executes continuously while the balance entered is not negative; in addition to calculating the fee, it prompts the user for and gets the balance for the next account. The end-of-job module executes after a number less than 0 is entered for the account balance.
Answers
The answer of drawing a hierarchy chart and then plan a logic of the program is given below:
What is a Program ?A program is a set of instructions that a computer can execute to perform a specific task or solve a particular problem. These instructions are typically written in a programming language and can range from simple calculations to complex algorithms.
a. Hierarchy chart:
+------------+
| Main Module|
+------------+
|
|
v
+-------------------+
| Housekeeping Module|
+-------------------+
|
|
v
+----------------+
| Detail Module |
+----------------+
|
|
v
+-------------------+
| End-of-Job Module |
+-------------------+
Logic Plan:
Define global variables balance and numOverdrafts.
Call the housekeeping module to prompt the user for and accept the account balance.
Call the detail module to prompt the user for and accept the number of overdrafts, compute the fee, and display the result.
Call the end-of-job module to display the message "Thanks for using this program".
Housekeeping module:
Prompt the user for and accept the account balance.
Detail module:
Prompt the user for and accept the number of overdrafts.
Compute the fee as 1% of the balance minus 5 dollars for each time the account was overdrawn.
Display the fee.
End-of-job module:
Display the message "Thanks for using this program".
b. Hierarchy chart:
+------------+
| Main Module|
+------------+
|
|
v
+-------------------+
| Housekeeping Module|
+-------------------+
|
|
v
+----------------+
| Detail Module |
+----------------+
|
|
v
+-------------------+
| End-of-Job Module |
+-------------------+
a. Hierarchy chart:
sql
Copy code
+------------+
| Main Module|
+------------+
|
|
v
+-------------------+
| Housekeeping Module|
+-------------------+
|
|
v
+----------------+
| Detail Module |
+----------------+
|
|
v
+-------------------+
| End-of-Job Module |
+-------------------+
Logic Plan:
Define global variables balance and numOverdrafts.
Call the housekeeping module to prompt the user for and accept the account balance.
Call the detail module to prompt the user for and accept the number of overdrafts, compute the fee, and display the result.
Call the end-of-job module to display the message "Thanks for using this program".
Housekeeping module:
Prompt the user for and accept the account balance.
Detail module:
Prompt the user for and accept the number of overdrafts.
Compute the fee as 1% of the balance minus 5 dollars for each time the account was overdrawn.
Display the fee.
End-of-job module:
Display the message "Thanks for using this program".
b. Hierarchy chart:
sql
Copy code
+------------+
| Main Module|
+------------+
|
|
v
+-------------------+
| Housekeeping Module|
+-------------------+
|
|
v
+----------------+
| Detail Module |
+----------------+
|
|
v
+-------------------+
| End-of-Job Module |
+-------------------+
Logic Plan:
Define global variables balance and numOverdrafts.
Call the housekeeping module to prompt the user for and accept the account balance.
While the balance entered is not negative, do the following:
a. Call the detail module to prompt the user for and accept the number of overdrafts, compute the fee, and display the result.
b. Prompt the user for and accept the balance for the next account.
Call the end-of-job module to display the message "Thanks for using this program".
Housekeeping module:
Prompt the user for and accept the account balance.
Detail module:
Prompt the user for and accept the number of overdrafts.
Display the fee.
End-of-job module:
Display message "Thanks for using this program"
To know more about Module visit:
https://brainly.com/question/30780451
#SPJ1
A(n) _____ is any piece of data that is passed into a function when the function is called.
Answers
Answer:
A parameter is a piece of information that is passed to a function to allow it to complete its task. A parameter can be any one of the four data types: handle, integer, object, or string.
Internet Retailing
Visit an e-commerce Web site such as Amazon.com and find a product you would like to purchase. While looking at the page for that item, count the number of other products that are being offered on that page.
Activity
Answer the following questions: What do they have in common? Why are they appearing on that page?
Answers
When I visited the e-commerce Web site such as Amazon.com and find a product that I would like to purchase which is a laptop, The thing that the sellers have in common is that they are trusted and verified sellers, their product presentation is nice and has warranty on it. The reason they are appearing on that page is because the product are similar.
What is E-commerce site website?The term e-commerce website is one that enables customers to buy and sell tangible products, services, and digital commodities over the internet as opposed to at a physical store. A company can process orders, receive payments, handle shipping and logistics, and offer customer care through an e-commerce website.
Note that there are numerous eCommerce platforms available, each with its own set of characteristics. The optimal eCommerce platform will therefore rely on your demands, available resources, and business objectives.
So, for instance, if you're a novice or small business owner looking to set up an online store in only a few clicks, go with a website builder like Hostinger. Oberlo, on the other hand, boasts the best inventory management system for dropshippers and is the top eCommerce platform overall.
Learn more about e-commerce Web site from
https://brainly.com/question/23369154
#SPJ1
What is social displacement? Question 22 options: the gained efficiency in being able to communicate through technology , the act of moving files from your computer to an external site , the risk of being "unfriended" by someone on social media , the reduced amount of time we spend communicating face to face
Answers
Answer: The Answer should be D
Explanation: It's the definition.
Which IP QoS mechanism involves prioritizing traffic? Group of answer choices IntServ RSVP COPS DiffServ None of the above
Answers
Answer:
DiffServ
Explanation:
The IP QoS which is fully known as QUALITY OF SERVICE mechanism that involves prioritizing traffic is DIFFERENTIATED SERVICES (DiffServ).
DIFFERENTIATED SERVICES help to differentiate ,arrange ,manage, control and focus on network traffic that are of great significance or important first before network that are less important or by their order of importance in order to provide quality of service and to avoid network traffic congestion which may want to reduce the quality of service when their is to much load on the network .
Assume the variable s is a String and index is an int. Write an if-else statement that assigns 100 to index if the value of s would come between "mortgage" and "mortuary" in the dictionary. Otherwise, assign 0 to index.
Answers
Using the knowledge in computational language in python it is possible to write a code that Assume the variable s is a String and index is an int.
Writting the code:Assume the variable s is a String
and index is an int
an if-else statement that assigns 100 to index
if the value of s would come between "mortgage" and "mortuary" in the dictionary
Otherwise, assign 0 to index
is
if(s.compareTo("mortgage")>0 && s.compareTo("mortuary")<0)
{
index = 100;
}
else
{
index = 0;
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

What keys on the keyboard have the ability to move the cursor around on a window?
No links and files or I report!
Will give Brainliest!
Answers
Answer:
Press the Windows key on your keyboard. In the box that appears, type Ease of Access mouse settings and press Enter . In the Mouse Keys section, toggle the switch under Use numeric pad to move mouse around the screen to On. Press Alt + F4 to exit this menu.
A macro is assigned as a button or a ___________ shortcut.
Answers
Answer:
Quick access toolbar
Exercise 8-3 Encapsulate
fruit = "banana"
count = 0
for char in fruit:
if char == "a":
count += 1
print(count)
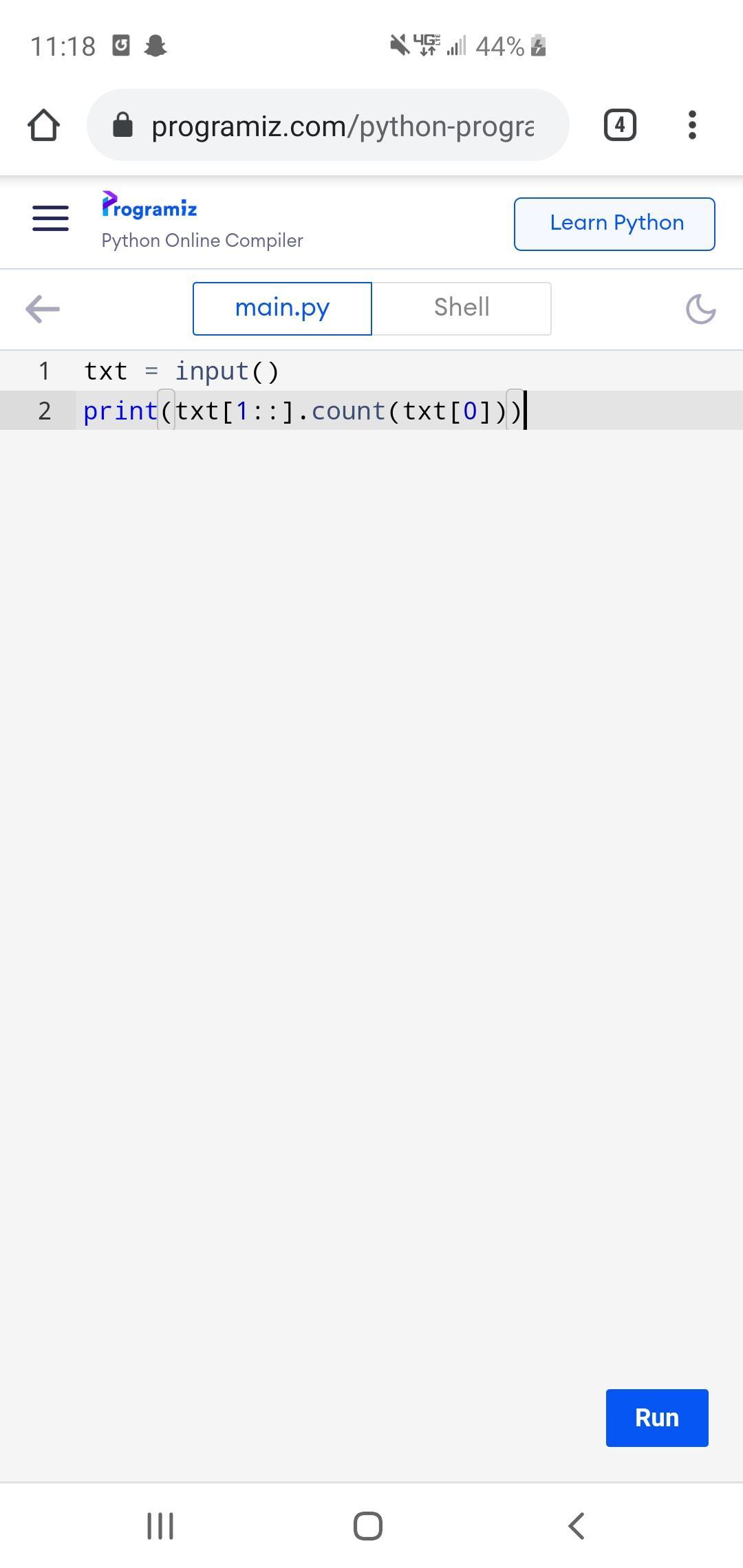
This code takes the word "banana" and counts the number of "a"s. Modify this code so that it will count any letter the user wants in a string that they input. For example, if the user entered "How now brown cow" as the string, and asked to count the w's, the program would say 4.
Put the code in a function that takes two parameters-- the text and the letter to be searched for. Your header will look like def count_letters(p, let) This function will return the number of occurrences of the letter.
Use a main() function to get the phrase and the letter from the user and pass them to the count_letters(p,let) function. Store the returned letter count in a variable. Print "there are x occurrences of y in thephrase" in this function.
Screen capture of input box to enter numbeer 1
Answers
Answer:
python
Explanation:
def count_letters(p, let):
count = 0
for char in p:
if char == let:
count += 1
print(f"There are {count} occurrences of {let} in the phrase {p}")
def main():
the_phrase = input("What phrase to analyze?\n")
the_letter = input("What letter to count?\n")
count_letters(the_phrase, the_letter)
main()